$16 Million Fine For T-Mobile: Details Of Three Years Of Data Security Lapses

Table of Contents
The Extent of the Data Breach: What Information Was Compromised?
The T-Mobile data breach exposed a significant amount of sensitive customer data. The scale of the compromise underscores the severity of the security failures and the potential risks faced by affected individuals. The compromised information included:
- Personal Identifiers: Names, addresses, phone numbers, email addresses.
- Financial Information: Account numbers, credit card details (in some cases).
- Sensitive Personal Data: Social Security numbers, driver's license numbers.
- Account Information: T-Mobile account details, including account numbers and service information.
The exact number of affected customers varied across the different incidents within the three-year period, but the cumulative impact on millions of individuals resulted in a substantial risk of identity theft and financial fraud. This customer data breach highlights the critical need for companies to prioritize data protection strategies, using keywords like customer data breach, sensitive information, personal data, data compromise, and identity theft risk to address the issue's significant implications.
Chronology of T-Mobile's Data Security Lapses (2020-2023): A Timeline of Failures
T-Mobile's data security failures weren't a single event but rather a series of incidents over three years. Understanding the timeline helps to illustrate the cumulative impact of these failures and the lack of proactive measures to prevent further breaches. Using keywords like timeline, data breach timeline, security incident, cybersecurity vulnerabilities, and data security failures, we can trace the failures:
The 2020 Data Breach:
This initial breach involved vulnerabilities in T-Mobile's systems that allowed unauthorized access to customer data. Specific details about the vulnerabilities exploited were not fully disclosed publicly, but investigations indicated weaknesses in network security protocols.
The 2021 Security Incident:
A separate security incident in 2021 revealed further weaknesses in T-Mobile's data protection. This incident highlighted the lack of comprehensive security monitoring and response systems, allowing the compromise to go undetected for an extended period.
The 2022 Vulnerability:
Another significant vulnerability in 2022 exposed additional customer data. This underscored a pattern of recurring security flaws and a failure to implement effective preventative measures. The pattern revealed a systemic problem within T-Mobile's security infrastructure.
The Regulatory Response: Why the $16 Million Fine?
The $16 million fine levied against T-Mobile resulted from investigations by the Federal Trade Commission (FTC) and potentially state attorneys general. The investigations determined that T-Mobile violated several consumer protection laws and regulations related to data security. The violations included a failure to implement reasonable security measures to protect customer data, resulting in substantial harm to consumers. The magnitude of the fine reflects the severity of the breaches, the number of affected individuals, and the potential for significant financial and reputational damage. Keywords like FTC fine, regulatory response, data breach penalties, legal consequences, cybersecurity regulations, and consumer protection laws help clarify the regulatory aspects.
Lessons Learned and Best Practices for Data Security
T-Mobile's experience underscores the critical need for proactive and comprehensive data security measures. Businesses of all sizes must prioritize data protection to avoid similar costly consequences. Key takeaways and best practices include:
- Regular Security Audits: Conduct frequent and thorough audits of systems and networks to identify vulnerabilities.
- Employee Training: Implement comprehensive cybersecurity awareness training for all employees.
- Strong Password Policies: Enforce strong password policies, including multi-factor authentication.
- Data Encryption: Encrypt sensitive data both in transit and at rest.
- Incident Response Planning: Develop and regularly test a comprehensive incident response plan.
- Vulnerability Management: Implement a robust vulnerability management program to identify and address security weaknesses promptly.
These data security best practices, along with keywords such as cybersecurity best practices, data protection, risk management, security audits, and incident response, should be central to any organization's security strategy.
Conclusion: Preventing Future T-Mobile-Style Data Security Lapses
The $16 million fine imposed on T-Mobile serves as a cautionary tale highlighting the severe financial and reputational risks associated with inadequate data security. The company's repeated failures over a three-year period demonstrate the importance of proactive measures and a robust security posture. Don't let your company become the next victim of a costly data breach. Learn more about strengthening your data security today! Prioritize data security, implement best practices, and protect your valuable customer data. Investing in robust data security is not merely a cost; it's an investment in the long-term health and success of your organization.

Featured Posts
-
 Etfs The Safe Haven For Investors During Market Instability
May 28, 2025
Etfs The Safe Haven For Investors During Market Instability
May 28, 2025 -
 Persemian Gerakan Bali Bersih Sampah Peran Masyarakat Dalam Mewujudkan Bali Yang Lebih Hijau
May 28, 2025
Persemian Gerakan Bali Bersih Sampah Peran Masyarakat Dalam Mewujudkan Bali Yang Lebih Hijau
May 28, 2025 -
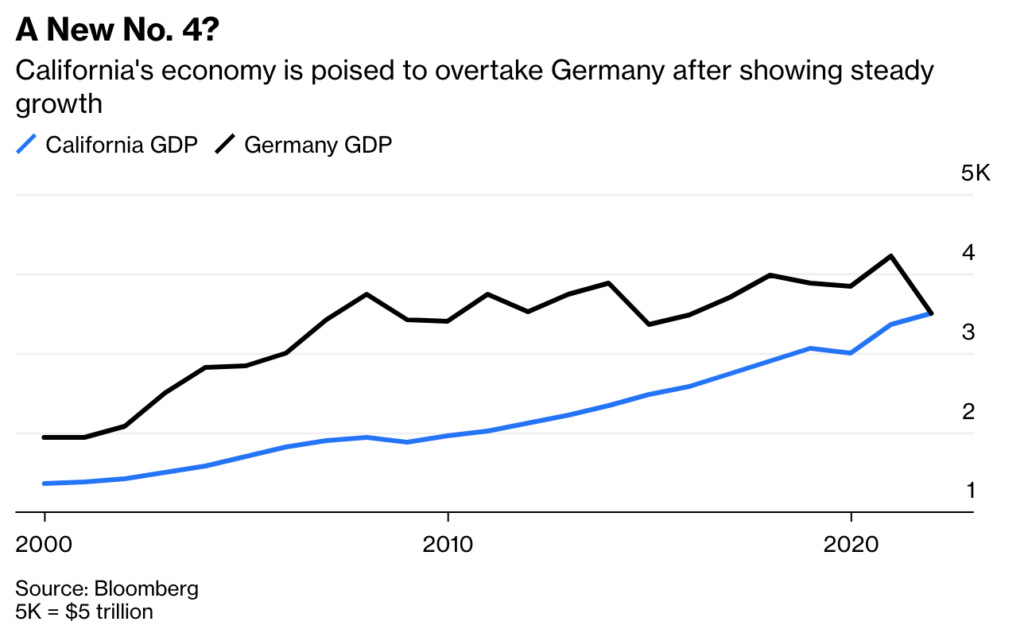 Life In California Vs Germany A Personal Account
May 28, 2025
Life In California Vs Germany A Personal Account
May 28, 2025 -
 Padres Vs Opponent Arraezs Absence Sheets Return
May 28, 2025
Padres Vs Opponent Arraezs Absence Sheets Return
May 28, 2025 -
 The Canadian Tire Hudsons Bay Merger Implications And Future Outlook
May 28, 2025
The Canadian Tire Hudsons Bay Merger Implications And Future Outlook
May 28, 2025
Latest Posts
-
 New Air Jordans May 2025 Release Dates And Details
May 29, 2025
New Air Jordans May 2025 Release Dates And Details
May 29, 2025 -
 All Air Jordans Releasing In June 2025 The Ultimate Sneakerheads Guide
May 29, 2025
All Air Jordans Releasing In June 2025 The Ultimate Sneakerheads Guide
May 29, 2025 -
 What Air Jordans Are Dropping In May 2025
May 29, 2025
What Air Jordans Are Dropping In May 2025
May 29, 2025 -
 Air Jordan June 2025 Release Calendar And Details
May 29, 2025
Air Jordan June 2025 Release Calendar And Details
May 29, 2025 -
 Air Jordan Sneaker Release Calendar May 2025
May 29, 2025
Air Jordan Sneaker Release Calendar May 2025
May 29, 2025
