Crook Accused Of Millions In Office365 Executive Email Account Breaches
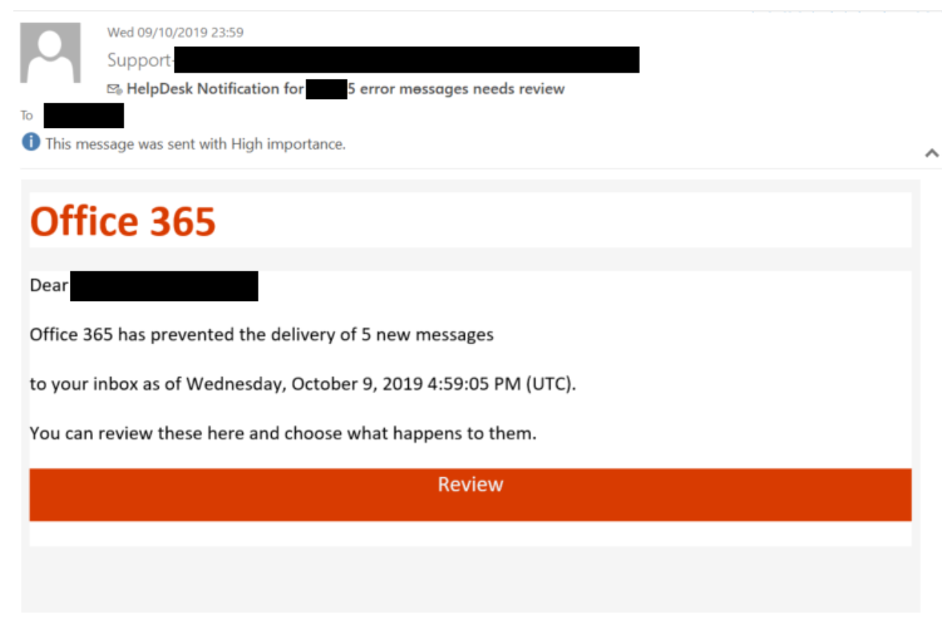
Table of Contents
Keywords: Office365 security breach, email account breach, executive email compromise, cybercrime, data breach, phishing, Office365 phishing, email security, data theft, million-dollar cybercrime
A sophisticated cybercriminal is accused of orchestrating a devastating Office365 security breach, resulting in millions of dollars in losses for a major unnamed corporation. This case highlights the critical vulnerability of executive email accounts and the urgent need for robust security measures to protect against increasingly sophisticated attacks. This article delves into the details of this significant Office365 phishing incident, exploring the methods used, the financial ramifications, and crucially, the steps organizations can take to prevent similar breaches.
The Alleged Crook and the Modus Operandi
While the identity of the accused remains undisclosed pending the ongoing investigation, law enforcement sources describe the perpetrator as a highly skilled individual with expertise in social engineering and exploiting vulnerabilities in cloud-based systems. The modus operandi involved a multi-stage attack leveraging both technical and psychological manipulation.
Phishing and Social Engineering Tactics
The attack began with a series of highly targeted spear phishing campaigns. These emails, meticulously crafted to appear legitimate and originating from trusted sources, were sent directly to executive-level employees.
- Spear Phishing Targeting Executives: Emails were personalized with details gleaned from public sources, creating a sense of authenticity and urgency.
- Sophisticated Social Engineering Techniques: The attacker employed psychological manipulation techniques, exploiting human trust and manipulating recipients into clicking malicious links or opening infected attachments.
- Exploiting Vulnerabilities in Office365 Systems: While specifics remain under investigation, it's suspected the attacker may have exploited known vulnerabilities in Office365, potentially related to outdated software or misconfigured settings.
- Use of Malicious Links and Attachments: The malicious links redirected victims to phishing websites designed to steal credentials, while the attachments contained malware capable of stealing data and granting persistent access to the victims’ accounts.
Data Exfiltration Methods
Once access was gained, the perpetrator systematically exfiltrated sensitive data using several methods:
- Forwarding Emails to External Accounts: Critically, emails containing financial data and sensitive communications were forwarded to external email accounts controlled by the attacker.
- Downloading Sensitive Files: Confidential documents, spreadsheets, and other files were downloaded directly from the compromised accounts.
- Utilizing Cloud Storage Services for Data Exfiltration: The attacker likely used cloud storage services to transfer large volumes of data discreetly and securely.
- Using Compromised Accounts to Access Other Systems: The compromised accounts may have served as a springboard to access other corporate systems and networks, expanding the scope of the breach.
The Financial Ramifications of the Office365 Breach
The financial impact of this Office365 breach is staggering. Initial reports suggest losses exceeding $5 million USD. This figure represents a significant blow to the victim organization and underscores the high cost of failing to implement adequate security measures.
Millions in Losses
The $5 million figure represents a preliminary estimate, and the final cost could be substantially higher as the full extent of the damage is assessed. The organization is still auditing its systems to determine the complete scope of the data theft and financial losses.
Types of Financial Losses
The losses incurred include:
- Wire Transfer Fraud: The attacker may have used compromised accounts to initiate fraudulent wire transfers to accounts under their control.
- Invoice Manipulation: Invoices may have been altered or created to redirect payments to fraudulent accounts.
- Identity Theft: Stolen data could lead to identity theft impacting both the organization and its employees.
- Intellectual Property Theft: The theft of intellectual property could result in substantial long-term financial losses.
The Ripple Effect
Beyond the direct financial losses, the breach has far-reaching consequences:
- Reputational Damage: The incident severely damages the organization's reputation, potentially impacting customer trust and future business opportunities.
- Legal Ramifications: The organization faces potential legal action from affected parties, regulatory bodies, and shareholders.
Preventing Office365 Executive Email Account Breaches
Preventing similar Office365 executive email account breaches requires a multi-layered approach encompassing technology, training, and policy.
Multi-Factor Authentication (MFA):
Implementing MFA is crucial. This adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain passwords.
Robust Security Awareness Training:
Regular and comprehensive security awareness training is essential for educating employees to recognize and avoid phishing emails and other social engineering tactics.
Regular Security Audits and Penetration Testing:
Regular security audits and penetration testing help identify vulnerabilities and weaknesses in your systems before attackers can exploit them.
Advanced Threat Protection (ATP) and Email Security Solutions:
Investing in advanced threat protection (ATP) and robust email security solutions helps filter out malicious emails and attachments before they reach employees' inboxes.
Enforce Strong Password Policies:
Enforce the use of strong, unique passwords that are regularly updated, and consider using a password manager.
Monitor Suspicious Login Attempts:
Set up monitoring systems to flag suspicious login attempts and unusual activity, alerting security personnel to potential threats.
Legal and Investigative Aspects
Law enforcement agencies are actively involved in investigating this Office365 data breach.
Law Enforcement Involvement:
The investigation involves collaboration between local, national, and potentially international agencies, given the potential transnational nature of such crimes.
Potential Charges and Penalties:
The accused faces potential charges related to cybercrime, fraud, data theft, and other relevant offenses. Penalties could include significant fines and imprisonment.
Victim Organization's Response:
The victim organization is cooperating fully with the investigation and is taking steps to improve its security posture to prevent future incidents.
Conclusion:
This Office365 security breach serves as a stark reminder of the devastating financial and reputational consequences of inadequate cybersecurity measures. The millions of dollars lost highlight the urgent need for organizations to prioritize email security and implement robust preventative measures. Protecting against sophisticated attacks requires a proactive approach, including multi-factor authentication, comprehensive employee training, and advanced threat protection. Protect your organization from devastating Office365 security breaches. Implement robust security measures and train your employees to identify phishing attempts today. [Link to Office365 Security Best Practices] [Link to Cybersecurity Training Resources]

Featured Posts
-
 College Van Omroepen Plannen Voor Herstel Vertrouwen Npo
May 15, 2025
College Van Omroepen Plannen Voor Herstel Vertrouwen Npo
May 15, 2025 -
 Giant Sea Wall Menko Ahy Pastikan Pembangunan Target Mulai
May 15, 2025
Giant Sea Wall Menko Ahy Pastikan Pembangunan Target Mulai
May 15, 2025 -
 Following The Dodgers Top Minor Leaguers Phillips Linan And Quinteros Progress
May 15, 2025
Following The Dodgers Top Minor Leaguers Phillips Linan And Quinteros Progress
May 15, 2025 -
 A Critical Look At Elizabeth Warrens Defense Of President Biden
May 15, 2025
A Critical Look At Elizabeth Warrens Defense Of President Biden
May 15, 2025 -
 Bim Aktueel Katalogu 25 26 Subat Iste Bu Haftanin Indirimli Ueruenleri
May 15, 2025
Bim Aktueel Katalogu 25 26 Subat Iste Bu Haftanin Indirimli Ueruenleri
May 15, 2025
