Cybercrime: Hacker Exploits Office365 To Steal Millions From Executives
Table of Contents
The Office365 Breach: How it Happened
This particular cybercrime leveraged a combination of social engineering and technical exploitation of Office365 vulnerabilities.
Phishing and Social Engineering
The attackers employed sophisticated spear-phishing emails, carefully crafted to appear legitimate and target high-level executives within the organization. These emails often contained urgent requests, mimicking internal communications or legitimate business transactions.
- Examples of convincing phishing emails: Emails impersonating CEOs requesting urgent wire transfers, emails containing seemingly legitimate invoices demanding immediate payment, emails with links to fake login pages mimicking the Office365 portal.
- Techniques to bypass multi-factor authentication (MFA): Attackers used various techniques, including brute-force attacks against weaker MFA methods, exploiting vulnerabilities in MFA implementation, and employing social engineering tactics to trick victims into sharing their authentication codes.
- Successful social engineering tactics: The attackers played on the urgency of the requests, leveraging the executives' trust in their colleagues and the perceived legitimacy of the communications.
Exploiting System Weaknesses
Beyond social engineering, the hackers likely exploited existing technical vulnerabilities within the victim's Office365 environment.
- Examples of exploited vulnerabilities: Unpatched software vulnerabilities in older versions of Office365 applications, misconfigured security settings allowing unauthorized access, weak or default passwords, lack of robust access controls.
- Importance of regular software updates and security audits: Regular patching and updates are crucial to prevent exploitation of known vulnerabilities. Similarly, regular security audits help identify and address misconfigurations and weaknesses before they can be exploited by attackers.
Post-Breach Activities
Once access was gained, the hackers maintained a persistent presence within the Office365 environment, meticulously planning the data exfiltration and fund transfer.
- Methods used to transfer money: The hackers likely used fraudulent wire transfers, manipulating payment information within the Office365 system to redirect funds to their controlled accounts. They may have also used other methods to conceal the fraudulent transactions.
- Challenges in tracing the funds once stolen: Tracing stolen funds in these sophisticated cyberattacks can be incredibly challenging, often involving international wire transfers and complex money laundering schemes. Law enforcement agencies frequently face significant obstacles in recovering the stolen assets.
The Impact of the Cybercrime
The consequences of this Office365 breach were far-reaching, extending beyond the immediate financial losses.
Financial Losses
The financial impact was substantial, with millions of dollars stolen from the organization’s accounts.
- Specific monetary amounts stolen: While precise figures are often kept confidential for security reasons, reports indicate millions of dollars were lost in this particular case.
- Potential impact on the company's financial stability: Such significant financial losses can severely impact a company's stability, potentially leading to job losses, reduced investment, and even bankruptcy in extreme cases.
Reputational Damage
The breach caused significant reputational damage to the affected company.
- Potential loss of investor confidence: News of a major data breach can erode investor confidence, leading to a decline in stock prices and difficulties securing future investments.
- Damage to customer trust: Customers may lose faith in a company's ability to protect their sensitive information, potentially resulting in lost business and damage to brand reputation.
- Negative media coverage: Negative media attention surrounding a major data breach can further amplify the reputational damage, creating lasting negative impacts.
Legal and Regulatory Implications
The legal and regulatory ramifications of such a breach are significant.
- Compliance issues: Non-compliance with data protection regulations, such as GDPR and CCPA, can result in hefty fines and legal penalties.
- Potential lawsuits from affected parties: The victims may face lawsuits from stakeholders affected by the breach, leading to further financial and legal burdens.
- Regulatory investigations: Regulatory bodies may launch investigations, leading to further scrutiny and potential fines.
Protecting Your Organization from Similar Attacks
Preventing similar Office365 breaches requires a multi-layered approach to cybersecurity.
Implementing Strong Security Measures
Robust security measures are essential to mitigate the risk of cyberattacks.
- Importance of robust MFA: Implementing strong multi-factor authentication (MFA) is crucial for preventing unauthorized access, even if passwords are compromised.
- Regular security awareness training for employees: Educating employees about phishing techniques and social engineering tactics is vital to reduce the likelihood of successful attacks.
- Using strong, unique passwords: Enforcing strong password policies and encouraging the use of unique passwords for all accounts is critical.
- Employing advanced threat protection solutions: Implementing advanced threat protection solutions, such as email security gateways and endpoint detection and response (EDR) systems, can help identify and block malicious attacks.
Regular Security Audits and Penetration Testing
Proactive security measures are crucial for identifying and mitigating vulnerabilities.
- Benefits of regular vulnerability assessments: Regular vulnerability assessments help identify weaknesses in your systems that could be exploited by attackers.
- Penetration testing: Penetration testing simulates real-world attacks to identify exploitable vulnerabilities before malicious actors can find them.
- Security audits: Regular security audits provide an independent assessment of your organization's security posture, helping to identify areas for improvement.
Incident Response Planning
Having a well-defined incident response plan is essential for minimizing the damage in case of a breach.
- Key elements of an effective incident response plan: A comprehensive plan should include communication protocols, incident containment strategies, data recovery procedures, and post-incident analysis.
- Importance of swift action in containing the damage during a breach: Swift action is critical to limit the impact of a cyberattack and prevent further damage.
Conclusion
This case study of cybercrime exploiting Office365 vulnerabilities highlights the devastating consequences of sophisticated attacks. Millions of dollars were lost, reputations tarnished, and legal ramifications ensued. The key takeaways are the critical need for strong MFA, regular security awareness training, robust threat protection solutions, and a proactive approach to security audits and incident response planning. Don't become the next victim. Strengthen your Office365 security today by implementing robust multi-factor authentication and regularly updating your software. Proactive security measures are your best defense against costly Office365 cybercrime.

Featured Posts
-
 Mlb Home Run Props Picks And Odds For May 8th Cant Stump The Schwarber
May 18, 2025
Mlb Home Run Props Picks And Odds For May 8th Cant Stump The Schwarber
May 18, 2025 -
 Kanye Westas Vel Provokuoja Paviesinta Biancos Censori Nuotraukos
May 18, 2025
Kanye Westas Vel Provokuoja Paviesinta Biancos Censori Nuotraukos
May 18, 2025 -
 Damiano David Un Artista Solista L Annuncio Ufficiale
May 18, 2025
Damiano David Un Artista Solista L Annuncio Ufficiale
May 18, 2025 -
 Exploring The Soundscapes Of Damiano Davids Funny Little Fears
May 18, 2025
Exploring The Soundscapes Of Damiano Davids Funny Little Fears
May 18, 2025 -
 Taylor Swifts 11 Albums Ranked And Reviewed
May 18, 2025
Taylor Swifts 11 Albums Ranked And Reviewed
May 18, 2025
Latest Posts
-
 Dodgers Left Handed Hitters Breaking The Slump
May 18, 2025
Dodgers Left Handed Hitters Breaking The Slump
May 18, 2025 -
 Dodgers Struggling Lefties Aim For A Comeback
May 18, 2025
Dodgers Struggling Lefties Aim For A Comeback
May 18, 2025 -
 Confortos Dodgers Debut Can He Follow In Hernandezs Footsteps
May 18, 2025
Confortos Dodgers Debut Can He Follow In Hernandezs Footsteps
May 18, 2025 -
 Can Conforto Replicate Hernandezs Success With The Dodgers
May 18, 2025
Can Conforto Replicate Hernandezs Success With The Dodgers
May 18, 2025 -
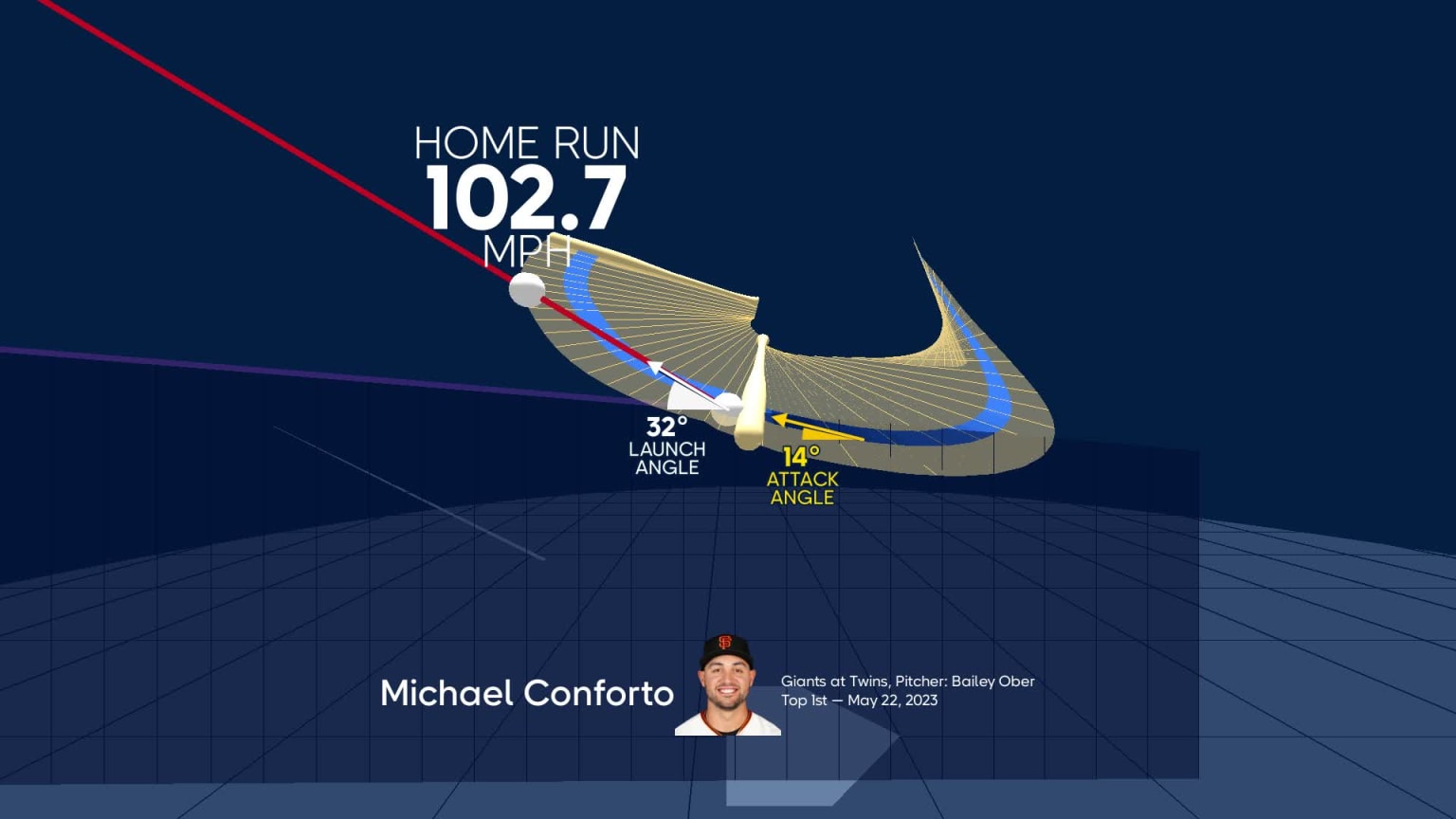 Analyzing Confortos Potential A Hernandez Comparison For The Dodgers
May 18, 2025
Analyzing Confortos Potential A Hernandez Comparison For The Dodgers
May 18, 2025
