Cybercrime Investigation: Hacker Profits Millions From Office365 Compromise
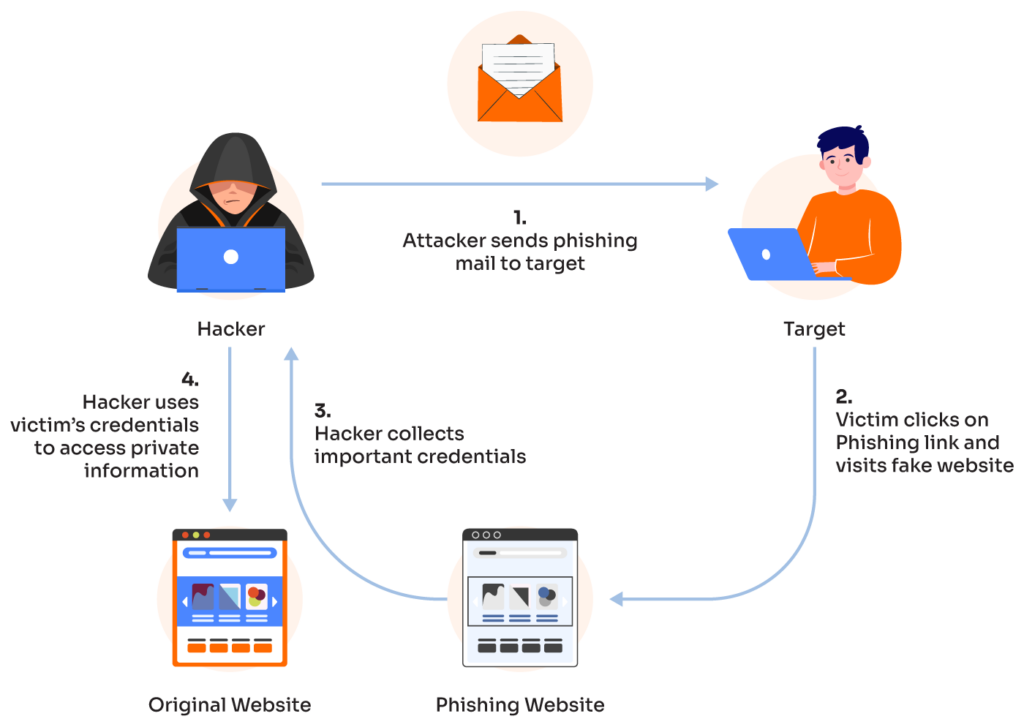
Table of Contents
The Hacker's Methodology: Exploiting Office365 Vulnerabilities
The hackers behind this significant data breach employed a multi-stage attack leveraging known vulnerabilities in Microsoft Office365. Their sophisticated approach highlights the evolving nature of cyber threats and the need for robust security measures.
Phishing and Social Engineering
The initial phase of the attack relied heavily on sophisticated phishing and social engineering techniques. The hackers crafted highly targeted phishing emails designed to appear legitimate, mimicking communications from trusted sources within the victim organizations.
- Examples of phishing emails: Emails appeared to be from internal IT staff requesting password resets, urgent invoice payments, or containing seemingly innocuous attachments. The emails often included company logos and branding for increased authenticity.
- Successful social engineering tactics: Hackers leveraged knowledge of internal company structures and employee roles to personalize their phishing attempts, increasing the likelihood of success. They exploited the human element, preying on urgency and trust.
- How credentials were stolen: Once victims clicked malicious links or opened infected attachments, malware was deployed, silently capturing their Office365 login credentials. This provided the hackers with an initial foothold into the network. Keywords: phishing attacks, social engineering, credential theft, spear phishing, email security.
Post-Exploitation Techniques
After gaining access, the hackers employed a range of advanced techniques to move laterally within the compromised networks and exfiltrate sensitive data. This demonstrates a high level of expertise and planning.
- Techniques used to move laterally within the network: The hackers utilized stolen credentials to access other accounts and systems within the organization's network. They leveraged vulnerabilities in applications and services to expand their access.
- Methods of data exfiltration (e.g., cloud storage, external servers): Stolen data was exfiltrated using various methods, including uploading data to cloud storage services and transferring it to external servers controlled by the hackers. They used obfuscation techniques to mask their activities.
- Obfuscation techniques used by the hackers: The hackers employed various techniques to hide their actions, including using encrypted communication channels and anonymizing tools to make it difficult to trace their activities. Keywords: lateral movement, data exfiltration, malware, ransomware, network security.
Monetizing the Breach
The stolen data was monetized through various illicit activities, resulting in significant financial losses for the victims.
- Examples of how stolen data was used (e.g., ransomware attacks, selling data on the dark web, identity theft): The hackers used the stolen data to launch ransomware attacks against some victims, demanding significant ransom payments for data recovery. In other cases, the data was sold on the dark web to other cybercriminals for further exploitation or used for identity theft.
- Financial implications for victims: The financial consequences for the victims included direct losses from ransom payments, legal fees, and remediation costs, as well as indirect losses from reputational damage, business disruption, and lost productivity. Keywords: ransomware, dark web, data monetization, identity theft, financial crime.
Impact of the Office365 Compromise
The Office365 compromise had a devastating impact on the affected organizations, extending beyond immediate financial losses.
Financial Losses
The financial losses incurred by the victims were substantial, reaching millions of dollars in total.
- Direct financial losses (e.g., ransom payments, legal fees): Victims incurred significant costs from paying ransoms, engaging forensic investigators, and dealing with legal ramifications.
- Indirect losses (e.g., loss of reputation, business disruption): The data breach also caused significant reputational damage, leading to loss of customer trust and business disruption. The cost of restoring normal operations and regaining customer confidence added to the overall financial burden. Keywords: financial losses, business disruption, reputational damage.
Data Loss and Privacy Concerns
The breach compromised a wide range of sensitive data, raising significant privacy concerns.
- Examples of compromised data (e.g., customer data, financial records, intellectual property): The stolen data included customer information, financial records, intellectual property, and other sensitive business information.
- Potential consequences for victims (e.g., identity theft, fraud): The victims faced the risk of identity theft, financial fraud, and other serious consequences as a result of the data breach. Compliance with regulations like GDPR and CCPA added further complexity and cost. Keywords: data loss, privacy violation, GDPR, CCPA, data protection.
Lessons Learned and Best Practices for Office365 Security
This cybercrime investigation underscores the importance of proactive security measures to protect against sophisticated attacks.
Enhancing Security Measures
Organizations need to implement robust security measures to safeguard their Office365 environments.
- Multi-factor authentication (MFA): Implementing MFA is crucial to add an extra layer of security and prevent unauthorized access even if credentials are compromised.
- Security awareness training for employees: Regular security awareness training can educate employees about phishing and social engineering tactics, reducing their vulnerability to attacks.
- Regular security audits: Conducting regular security audits can identify vulnerabilities and weaknesses in the system, allowing for timely remediation.
- Implementing advanced threat protection: Advanced threat protection solutions can detect and prevent malicious activities in real-time.
- Data loss prevention (DLP) solutions: DLP solutions can monitor and prevent sensitive data from leaving the organization’s network. Keywords: multi-factor authentication, MFA, security awareness training, security audit, threat protection, data loss prevention, DLP.
Incident Response Planning
A well-defined incident response plan is crucial for minimizing the impact of a data breach.
- Steps to take in case of a breach, including containing the attack, investigating the incident, and recovering from the breach: A robust plan should detail steps to contain the attack, investigate the root cause, recover from the breach, and notify affected individuals. This plan should be tested regularly to ensure its effectiveness. Keywords: incident response, cyber incident response plan, breach response, data recovery.
Conclusion
This cybercrime investigation into the massive Office365 compromise highlights the severe consequences of neglecting cybersecurity best practices. The millions lost underscore the critical need for robust security measures to protect against sophisticated hacking techniques. By implementing strong authentication, regular security audits, and comprehensive employee training, organizations can significantly reduce their vulnerability to similar attacks. Don't let your organization become the next victim; prioritize robust Office365 security today. Invest in comprehensive cybercrime investigation preparation and proactive security measures to safeguard your data and prevent devastating financial losses.

Featured Posts
-
 Huizenprijzen Nederland Verschilt De Mening Van Geen Stijl En Abn Amro
May 22, 2025
Huizenprijzen Nederland Verschilt De Mening Van Geen Stijl En Abn Amro
May 22, 2025 -
 Fans React To Peppa Pigs Mums Baby Gender Reveal
May 22, 2025
Fans React To Peppa Pigs Mums Baby Gender Reveal
May 22, 2025 -
 Wordle 1389 Hints Answer And Solution For April 8th Nyt
May 22, 2025
Wordle 1389 Hints Answer And Solution For April 8th Nyt
May 22, 2025 -
 Cau Ma Da Khoi Cong Xay Dung Thang 6 Noi Lien Dong Nai Va Binh Phuoc
May 22, 2025
Cau Ma Da Khoi Cong Xay Dung Thang 6 Noi Lien Dong Nai Va Binh Phuoc
May 22, 2025 -
 Middle Managers The Unsung Heroes Of Business Success
May 22, 2025
Middle Managers The Unsung Heroes Of Business Success
May 22, 2025
Latest Posts
-
 Solve Wordle Today March 6th Hints And Answer For 1356
May 22, 2025
Solve Wordle Today March 6th Hints And Answer For 1356
May 22, 2025 -
 Wordle 1356 March 6th Clues And Solution
May 22, 2025
Wordle 1356 March 6th Clues And Solution
May 22, 2025 -
 Wordle 370 March 20th Hints Clues And Answer
May 22, 2025
Wordle 370 March 20th Hints Clues And Answer
May 22, 2025 -
 Wordle 370 Hints And Answer For Thursday March 20th
May 22, 2025
Wordle 370 Hints And Answer For Thursday March 20th
May 22, 2025 -
 Wordle Hints And Answer Saturday March 8th Game 1358
May 22, 2025
Wordle Hints And Answer Saturday March 8th Game 1358
May 22, 2025
