Cybercriminal Made Millions Targeting Executive Office365 Accounts
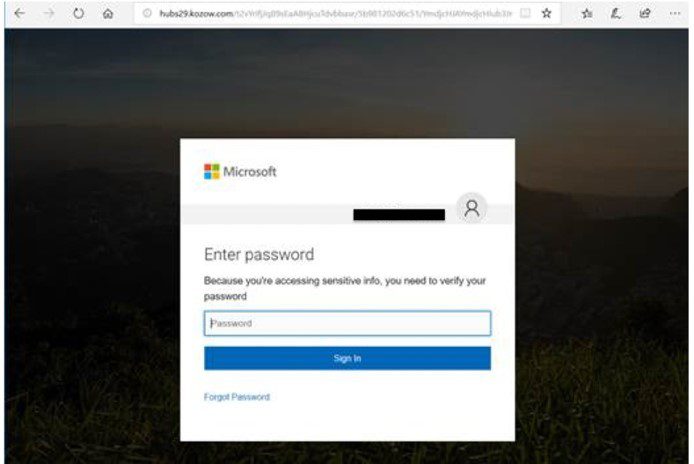
Table of Contents
The Sophistication of the Attack
This wasn't a simple phishing scam; this was a highly targeted and sophisticated operation. The cybercriminal employed advanced techniques to bypass security protocols and gain access to sensitive information.
Advanced Phishing Techniques
The attacks relied heavily on highly effective phishing strategies designed to deceive even the most cautious executives. These weren't generic phishing emails; they were meticulously crafted to appear legitimate.
- Spear Phishing: Emails were personalized, using information gleaned from social media and other public sources to create a sense of familiarity and trust.
- Whaling: The attacker specifically targeted high-profile executives, knowing that compromising their accounts would yield the greatest financial reward.
- Realistic Email Templates: Emails mimicked legitimate communications, using official branding and language to bypass spam filters.
- Forged Sender Addresses: Emails appeared to originate from trusted sources, such as colleagues, clients, or even the CEO themselves.
- Urgent Requests: Emails often contained urgent requests, creating a sense of pressure and urgency, encouraging immediate action without careful consideration.
- Links to Fake Login Pages: These convincing fake login pages were designed to steal usernames and passwords, providing access to the target's Office365 account.
- Social Engineering: The attackers used social engineering tactics, leveraging psychological manipulation to gain the trust of their victims. Building rapport and exploiting human nature were key elements of their success.
Exploiting Weaknesses in Multi-Factor Authentication (MFA)
While MFA is a crucial security layer, the cybercriminal found ways to circumvent or exploit weaknesses in its implementation. This highlights the fact that even robust security measures can be compromised if not properly configured and maintained.
- Vulnerabilities in MFA Implementation: Potential weaknesses included poorly implemented MFA processes, weak or easily guessed secondary authentication methods, and insufficient user training on MFA best practices.
- Importance of Strong Password Policies: Strong, unique passwords, regularly updated, remain essential, even with MFA in place. Password managers can help in this regard.
- Robust MFA Systems: Organizations should invest in robust and modern MFA solutions, utilizing a variety of authentication factors beyond simple SMS codes.
The Financial Impact and Data Breach
The consequences of this successful Office365 security breach were severe, impacting both the targeted organizations and their clients.
Financial Losses
The financial repercussions extended far beyond the initial monetary loss.
- Wire Transfer Fraud: The cybercriminal successfully initiated fraudulent wire transfers, diverting significant funds from the victim's accounts.
- Ransomware Payments: In some cases, ransomware was deployed, forcing victims to pay ransoms to regain access to their data.
- Legal Fees: Organizations incurred substantial legal fees in managing the aftermath of the breach, including investigations and regulatory compliance efforts.
- Reputational Damage: The breach significantly damaged the reputation of affected companies, eroding customer trust and impacting future business prospects.
- Business Disruption: The attack caused significant business disruption, halting operations and resulting in lost productivity and revenue.
Data Breaches and Sensitive Information
The stolen data included highly sensitive information with far-reaching consequences.
- Financial Data: Bank account details, credit card information, and other financial records were compromised.
- Intellectual Property: Confidential business plans, trade secrets, and other intellectual property were stolen, potentially giving competitors a significant advantage.
- Customer Information: Sensitive customer data, including personal details and financial information, were exposed, creating significant risks for both the company and its clients.
- Strategic Plans: Confidential strategic plans and business documents were compromised, potentially impacting future decision-making and business strategies.
- Regulatory Compliance Implications: Breaches of this nature trigger significant regulatory compliance implications under laws like GDPR and CCPA, leading to potential hefty fines and legal action.
Prevention and Mitigation Strategies
Protecting against these sophisticated attacks requires a multi-layered approach focusing on proactive security measures and robust response plans.
Strengthening Office365 Security
Proactive measures are key to preventing Office365 security breaches.
- Robust Multi-Factor Authentication (MFA): Implement strong MFA across all accounts, utilizing diverse authentication methods.
- Regular Security Awareness Training: Educate employees about phishing techniques, social engineering tactics, and secure password practices. Regular training and simulated phishing exercises are crucial.
- Strong Password Policies: Enforce strict password policies, requiring strong, unique passwords and regular changes. Password managers are highly recommended.
- Advanced Threat Protection: Enable advanced threat protection features within Office365 to detect and block malicious emails and attachments.
- Email Authentication Protocols (SPF, DKIM, DMARC): Implement these protocols to verify the authenticity of emails and prevent spoofing.
- Regular Security Audits: Conduct regular security audits to identify and address vulnerabilities in your Office365 environment.
- Software Patching and Updates: Keep all software and applications updated with the latest security patches.
Responding to a Potential Breach
A swift and decisive response is crucial in minimizing damage during a breach.
- Immediate Investigation: Immediately investigate any suspected breach, isolating affected accounts and systems.
- Containment of the Breach: Take immediate steps to contain the breach, preventing further spread of the attack.
- Notification of Affected Parties: Notify affected parties, including customers and regulatory bodies, as required by law.
- Law Enforcement Involvement: Report the breach to law enforcement agencies and cooperate fully with their investigation.
- Data Recovery and Restoration: Implement data recovery and restoration procedures to restore affected systems and data.
Conclusion
The case of the cybercriminal who made millions targeting executive Office365 accounts serves as a stark reminder of the ever-evolving threats in the digital landscape. The financial and reputational consequences of such attacks can be devastating. Therefore, prioritizing Office365 security is no longer optional; it's essential for survival. Businesses must invest in robust security measures, implement strong password policies, provide regular security awareness training for employees, and establish comprehensive incident response plans. Secure your Office365 environment today; prevent Office365 breaches by strengthening your Office365 security posture and exploring effective Office365 security solutions. Don't wait until it's too late; proactive security measures are the best defense against these sophisticated cyberattacks.

Featured Posts
-
 Ftcs Appeal Could Block Microsofts Activision Blizzard Acquisition
Apr 22, 2025
Ftcs Appeal Could Block Microsofts Activision Blizzard Acquisition
Apr 22, 2025 -
 Full List Celebrities Affected By The Palisades Fires In Los Angeles
Apr 22, 2025
Full List Celebrities Affected By The Palisades Fires In Los Angeles
Apr 22, 2025 -
 The Obamacare Supreme Court Case Analyzing Trumps Involvement And Its Effect On Rfk Jr
Apr 22, 2025
The Obamacare Supreme Court Case Analyzing Trumps Involvement And Its Effect On Rfk Jr
Apr 22, 2025 -
 Assessing The Impact Of Tariffs On Chinas Exports
Apr 22, 2025
Assessing The Impact Of Tariffs On Chinas Exports
Apr 22, 2025 -
 The Pan Nordic Military Evaluating The Roles Of Sweden And Finland
Apr 22, 2025
The Pan Nordic Military Evaluating The Roles Of Sweden And Finland
Apr 22, 2025
Latest Posts
-
 Lynk Lee Sau Chuyen Gioi Hanh Trinh Lot Xac Ngoan Muc Va Tinh Yeu Vung Ben
May 09, 2025
Lynk Lee Sau Chuyen Gioi Hanh Trinh Lot Xac Ngoan Muc Va Tinh Yeu Vung Ben
May 09, 2025 -
 The Kreischer Marriage Wifes Perspective On His Netflix Stand Up Comedy And Sex Jokes
May 09, 2025
The Kreischer Marriage Wifes Perspective On His Netflix Stand Up Comedy And Sex Jokes
May 09, 2025 -
 The 10 Best Film Noir Movies For A Classic Film Fix
May 09, 2025
The 10 Best Film Noir Movies For A Classic Film Fix
May 09, 2025 -
 Bert Kreischers Netflix Specials A Look At His Marriage And Risque Humor
May 09, 2025
Bert Kreischers Netflix Specials A Look At His Marriage And Risque Humor
May 09, 2025 -
 Top 10 Film Noir Movies From Beginning To End
May 09, 2025
Top 10 Film Noir Movies From Beginning To End
May 09, 2025
