Exec Office365 Breaches Net Millions For Crook, FBI Claims

Table of Contents
The Scale and Impact of the Office365 Breaches
The financial impact of compromised executive Office365 accounts is staggering. The FBI investigation uncovered losses amounting to millions of dollars, a figure likely underrepresenting the true extent of the problem due to underreporting. These breaches represent more than just financial loss; they inflict significant damage across multiple areas:
- Financial Impact: The direct financial losses from stolen funds, fraudulent transactions, and ransom payments are substantial. The average cost of an Office365 breach targeting executives is significantly higher than those targeting lower-level employees due to the access and authority held by these individuals.
- Data Theft: Breaches result in the theft of sensitive business information, including intellectual property, confidential client data, strategic plans, and financial records. This stolen information can be sold on the dark web or used for competitive advantage, causing long-term harm.
- Reputational Damage: A high-profile Office365 breach severely damages a company's reputation, eroding customer trust and impacting investor confidence. The resulting negative publicity can be devastating, leading to a loss of business and market share.
- Legal Consequences: Businesses facing an Office365 breach may face hefty fines and legal action due to non-compliance with data protection regulations like GDPR and CCPA. The legal costs associated with defending against lawsuits and resolving regulatory issues can be substantial.
Common Tactics Used in Office365 Breaches Targeting Executives
Cybercriminals employ sophisticated techniques to target executive Office365 accounts. These attacks are carefully planned and executed, leveraging the trust and authority associated with executive roles. Common tactics include:
- Spear Phishing Attacks: These highly targeted phishing emails use personalized information to deceive recipients into clicking malicious links or opening infected attachments. The emails often mimic legitimate communications from trusted sources, making them difficult to detect.
- Malware Infections: Malicious attachments or links in phishing emails can deliver malware, such as keyloggers, that steal login credentials or ransomware that encrypts data and demands a ransom for its release. These infections often go undetected for extended periods, allowing attackers to operate undetected.
- Credential Stuffing Attacks: Attackers use stolen credentials from other platforms (data breaches on other sites) to attempt to access Office365 accounts. This method relies on the reuse of passwords across multiple platforms – a common and dangerous practice.
- Ransomware Attacks: Increasingly, ransomware is used to encrypt sensitive data, demanding a ransom for its release. The threat of data loss and business disruption compels victims to pay, further fueling the profitability of these attacks.
Best Practices for Preventing Office365 Breaches
Proactive security measures are crucial in preventing costly Office365 breaches. Implementing these best practices can significantly reduce your risk:
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of authentication to access accounts, even if a password is compromised. This is a critical first step.
- Security Awareness Training: Regular security awareness training for all employees is essential. Educate your staff about phishing, social engineering techniques, and safe internet practices. Simulate phishing attacks to test employees' awareness.
- Strong Password Policies: Enforce strong password policies, including password complexity requirements and regular password changes. Encourage the use of password managers to help manage and generate strong unique passwords.
- Regular Security Updates: Keep all software and applications, including Office365, updated with the latest security patches. This helps to patch vulnerabilities that attackers could exploit.
- Data Loss Prevention (DLP): Implement DLP tools to monitor and control the movement of sensitive data, preventing unauthorized access and exfiltration.
- Threat Intelligence: Utilize threat intelligence feeds to stay informed about emerging threats and vulnerabilities, allowing for proactive mitigation strategies.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to monitor endpoints for malicious activity and respond to threats in real-time. This provides advanced threat detection and response capabilities.
Responding to an Office365 Breach
Even with the best security measures, breaches can still occur. Having a well-defined incident response plan is crucial:
- Incident Response Plan: Develop a comprehensive plan outlining the steps to take in case of a breach, including communication protocols, forensic investigation procedures, and data recovery strategies.
- Forensic Investigation: Engage a forensic investigator to determine the extent of the breach, identify the root cause, and gather evidence for legal and insurance purposes.
- Data Recovery: Implement data recovery procedures to restore compromised data if possible. Regular backups are vital in this process.
- Legal Counsel: Seek legal counsel to understand your legal obligations, navigate regulatory requirements, and manage potential litigation.
- Communication Strategy: Develop a clear communication strategy to inform stakeholders (employees, customers, investors, and regulators) of the breach and its impact in a timely and transparent manner.
Conclusion
The FBI's findings highlight the devastating consequences of unchecked Office365 breaches, costing executives and their companies millions. The financial losses, reputational damage, and legal repercussions are simply too great to ignore. By prioritizing robust cybersecurity measures, including multi-factor authentication, comprehensive security awareness training, and a well-defined incident response plan, businesses can significantly reduce their vulnerability to these costly attacks. Don't wait for an Office365 breach to cripple your organization – strengthen your Office365 security today. Invest in the right tools and training to protect your executive accounts and prevent potentially catastrophic financial and reputational losses.

Featured Posts
-
 16 Year Old Victim Of Gay Bashing Five Teen Arrests Made
May 29, 2025
16 Year Old Victim Of Gay Bashing Five Teen Arrests Made
May 29, 2025 -
 Diddy Sex Party Male Escort Issues Public Apology To Cassie
May 29, 2025
Diddy Sex Party Male Escort Issues Public Apology To Cassie
May 29, 2025 -
 California High School Athletes Bay Areas Best Vote Now
May 29, 2025
California High School Athletes Bay Areas Best Vote Now
May 29, 2025 -
 Wie Moet Ajax Aanstellen Van Hanegem Geeft Advies
May 29, 2025
Wie Moet Ajax Aanstellen Van Hanegem Geeft Advies
May 29, 2025 -
 A Comprehensive Guide To Probopass Ex Decks In Pokemon Tcg Pocket
May 29, 2025
A Comprehensive Guide To Probopass Ex Decks In Pokemon Tcg Pocket
May 29, 2025
Latest Posts
-
 Fda Grants Fast Track Designation To Sanofis Chlamydia Vaccine
May 31, 2025
Fda Grants Fast Track Designation To Sanofis Chlamydia Vaccine
May 31, 2025 -
 Sanofi Inauguration D Un Nouveau Site De Production En France Communique De Presse Officiel
May 31, 2025
Sanofi Inauguration D Un Nouveau Site De Production En France Communique De Presse Officiel
May 31, 2025 -
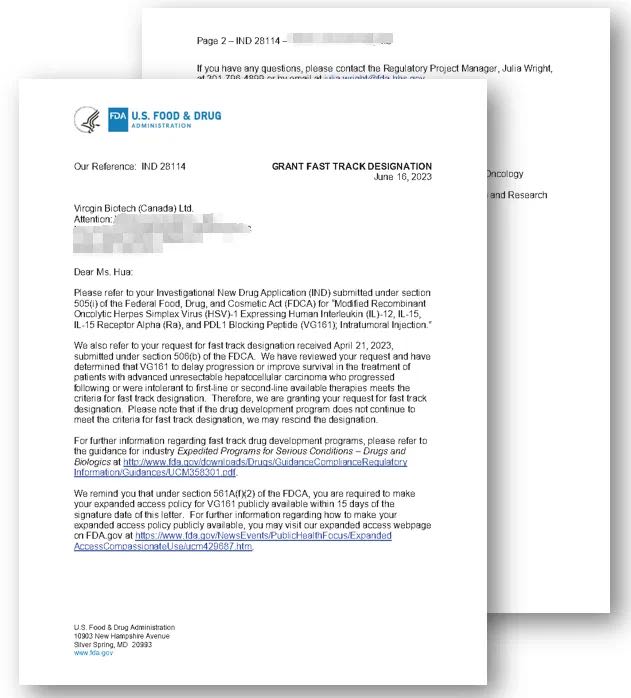 Sanofis Chlamydia Vaccine Candidate Receives Fda Fast Track Designation
May 31, 2025
Sanofis Chlamydia Vaccine Candidate Receives Fda Fast Track Designation
May 31, 2025 -
 Sanofi Inaugure Un Nouveau Site En France Communique De Presse
May 31, 2025
Sanofi Inaugure Un Nouveau Site En France Communique De Presse
May 31, 2025 -
 1 9 Milliarden Dollar Sanofis Grosser Schritt Im Kampf Gegen Autoimmunerkrankungen
May 31, 2025
1 9 Milliarden Dollar Sanofis Grosser Schritt Im Kampf Gegen Autoimmunerkrankungen
May 31, 2025
