Hegseth's Signal Chats: Military Plans Discussed With Family
Table of Contents
Security Concerns Raised by Family Discussions of Military Plans
The act of discussing military plans, even within the seemingly safe confines of a family, presents inherent security risks. Disclosing sensitive military information, regardless of intent, can have catastrophic consequences for national security. A seemingly innocuous conversation could inadvertently compromise ongoing operations or lead to a devastating data breach.
The potential consequences of such leaks are severe:
- Risk of accidental disclosure through casual conversation: Unintentional slips of the tongue can reveal crucial details.
- Potential for eavesdropping or unauthorized access to information: Family members, friends, or even sophisticated surveillance could intercept sensitive conversations.
- The danger of compromised family members: A family member, facing pressure or coercion, could divulge information to adversaries.
- Legal ramifications of such disclosures: The unauthorized disclosure of classified information carries significant legal penalties.
These risks highlight the critical importance of strict adherence to information security protocols within the military and related circles. Keywords like national security, military secrets, information security, data breach, and classified information underscore the gravity of this issue.
Hegseth's Public Persona and the Impact on Perception
Pete Hegseth's prominent public persona as a media personality and commentator significantly influences public perception. His opinions on military matters carry considerable weight, making his actions subject to heightened scrutiny. The reported "Hegseth's Signal Chats" have raised questions about his judgment and potentially damaged public trust in military leadership.
- Hegseth's role as a media personality and commentator: His high profile amplifies the impact of his actions.
- The influence of his opinions on public discourse about military matters: His pronouncements shape public opinion.
- The potential for misinterpretations or distortions of his actions: Any perceived lapse in security can be easily magnified and distorted.
Therefore, understanding the impact of his actions on public image, media scrutiny, reputation management, public trust, and military leadership is crucial.
Comparison to Similar Incidents and Precedents
History is replete with instances where informal discussions of military plans within families have resulted in disastrous consequences. Analyzing these historical precedents and case studies provides valuable insights into the potential ramifications of Hegseth's actions. While specific details surrounding Hegseth's case may differ, the underlying principle remains the same: the unauthorized disclosure of military secrets poses a significant threat to national security. The lack of established, universally recognized protocols regarding family communication about sensitive military information further exacerbates the problem. Examining military protocols and past security breaches helps define best practices for handling such situations.
The Role of Technology in Secure Communication
The risks associated with informal communication can be mitigated through the use of secure communication technologies. Employing robust data encryption and utilizing secure communication platforms is paramount for protecting sensitive information.
- Importance of using encrypted communication channels: Encryption protects information from unauthorized access.
- Best practices for secure data handling and storage: Following established protocols is essential.
- The role of technology in protecting sensitive information: Technology plays a crucial role in modern cybersecurity and information protection.
Understanding and implementing these technological safeguards is crucial for maintaining secure communication and upholding national security.
Conclusion: Understanding the Implications of Hegseth's Signal Chats
The reported "Hegseth's Signal Chats" highlight the critical need for robust information security practices within the military and related sectors. The potential consequences of even seemingly harmless family discussions regarding military plans can be catastrophic, impacting national security and eroding public trust. Analyzing Hegseth's Signal Chats reveals not only the security risks but also the ethical responsibilities of those handling sensitive information. We must prioritize secure communication and stringent protocols to safeguard national interests. Understanding the risks of Hegseth-style communications and the implications of Hegseth's family communications should be a priority for anyone involved in handling sensitive information. We urge further investigation into the complexities of military information security and the ethical responsibilities involved.

Featured Posts
-
 Winners And Losers Assessing The Impact Of Trumps Economic Policies
Apr 22, 2025
Winners And Losers Assessing The Impact Of Trumps Economic Policies
Apr 22, 2025 -
 Understanding Papal Conclaves History Secrecy And The Election Of The Pope
Apr 22, 2025
Understanding Papal Conclaves History Secrecy And The Election Of The Pope
Apr 22, 2025 -
 Rallying Against Trump Protester Perspectives From Across The Us
Apr 22, 2025
Rallying Against Trump Protester Perspectives From Across The Us
Apr 22, 2025 -
 Examining The Feasibility Of A Joint Swedish Finnish Defense Partnership
Apr 22, 2025
Examining The Feasibility Of A Joint Swedish Finnish Defense Partnership
Apr 22, 2025 -
 Assessing The Impact Of Tariffs On Chinas Exports
Apr 22, 2025
Assessing The Impact Of Tariffs On Chinas Exports
Apr 22, 2025
Latest Posts
-
 Edmonton School Projects 14 Initiatives To Proceed Rapidly
May 10, 2025
Edmonton School Projects 14 Initiatives To Proceed Rapidly
May 10, 2025 -
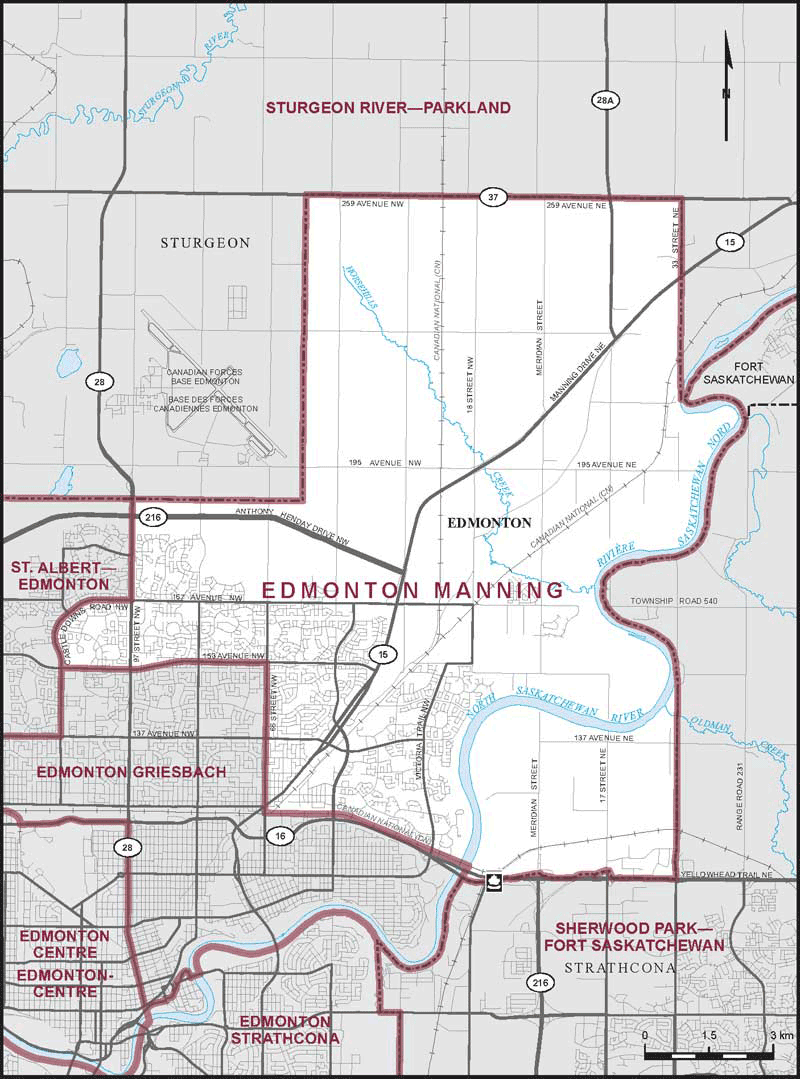 Understanding The Impact Of Federal Riding Changes In Greater Edmonton
May 10, 2025
Understanding The Impact Of Federal Riding Changes In Greater Edmonton
May 10, 2025 -
 Edmonton Unlimiteds Global Impact Strategy Scaling Tech And Innovation
May 10, 2025
Edmonton Unlimiteds Global Impact Strategy Scaling Tech And Innovation
May 10, 2025 -
 Federal Riding Boundary Changes Their Effect On Edmonton Area Voters
May 10, 2025
Federal Riding Boundary Changes Their Effect On Edmonton Area Voters
May 10, 2025 -
 Edmonton Unlimiteds New Tech And Innovation Strategy Scaling For Global Impact
May 10, 2025
Edmonton Unlimiteds New Tech And Innovation Strategy Scaling For Global Impact
May 10, 2025
