Millions Stolen: Insider Reveals Exec Office365 Account Compromise
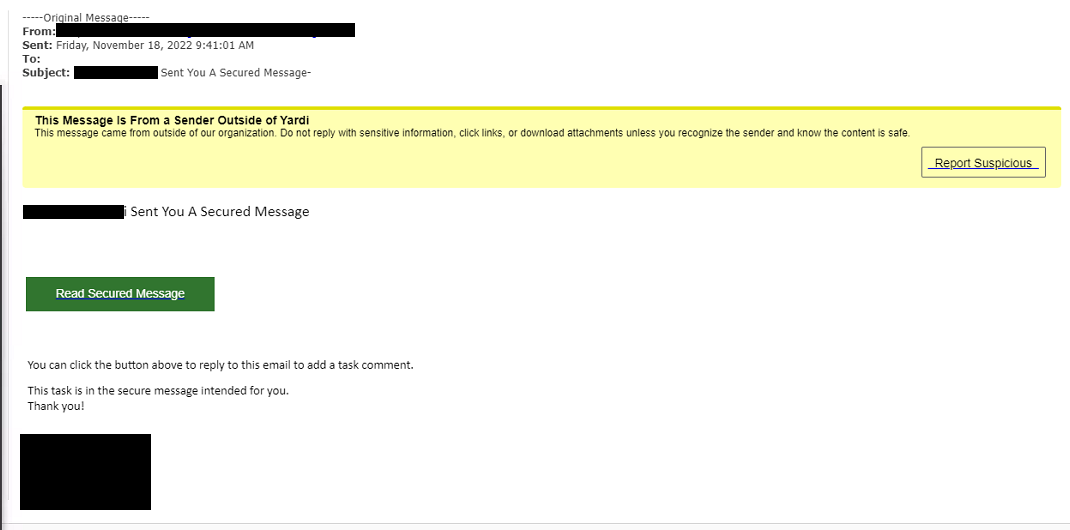
Table of Contents
The Insider Threat: How It Happened
This devastating Office365 security breach wasn't the result of a sophisticated external attack; it was an insider threat. The perpetrator, a disgruntled mid-level employee with access to executive accounts, exploited a combination of vulnerabilities to gain unauthorized access. This highlights the often-overlooked danger of employee negligence and the significant risk posed by compromised credentials.
-
The Insider's Motivation: Driven by a desire for financial gain and fueled by resentment over a recent performance review, the employee sought to inflict maximum damage.
-
Method of Compromise: The attack leveraged a sophisticated phishing email, cleverly disguised as a legitimate company communication. This email contained a malicious link leading to a fake login page designed to steal the executive's credentials. The success of this attack points to the importance of robust cybersecurity awareness training.
-
Failure of Security Measures: Critically, multi-factor authentication (MFA) was not implemented for executive accounts. This single omission proved fatal, rendering the compromised credentials instantly usable. The lack of MFA significantly reduced the security posture and allowed the attacker easy access.
-
Vulnerability Exploitation: The attacker exploited the weakness of a single, easily guessed password. This underscores the vital importance of enforcing strong password policies and promoting good password hygiene among all employees.
-
Example Phishing Email: The phishing email mimicked a legitimate email from the CEO, requesting urgent action on a supposed financial transaction. This highly targeted approach exemplified social engineering techniques used to bypass security protocols.
The Scale of the Data Breach: What Was Stolen?
The consequences of this executive Office365 security breach are staggering. The stolen data included:
-
Financial Data: Millions of dollars were directly transferred from company accounts to offshore accounts controlled by the attacker.
-
Confidential Information: Sensitive business strategies, upcoming product launches, and crucial financial forecasts were all accessed and potentially leaked.
-
Customer Data: Personal information belonging to thousands of clients was compromised, leading to significant privacy violations and potential legal repercussions.
-
Intellectual Property: Proprietary research and development data were stolen, putting the company’s competitive edge at risk.
The long-term impact of this data loss includes substantial financial losses, irreversible reputational damage, legal battles, and a loss of customer trust. The incident serves as a stark reminder of the far-reaching consequences of inadequate cloud security measures.
Lessons Learned: Strengthening Office365 Security
This case study offers crucial lessons for organizations seeking to prevent similar Office365 account compromises. Implementing robust security measures is paramount, including:
-
Multi-Factor Authentication (MFA): Implementing MFA for all accounts, especially executive-level access, is non-negotiable. This adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access even with stolen credentials.
-
Robust Password Management: Enforce strong, unique passwords and encourage the use of password managers. Regular password changes and complex password policies are essential.
-
Cybersecurity Awareness Training: Invest in comprehensive and regular cybersecurity awareness training for all employees to educate them about phishing scams, social engineering tactics, and best security practices.
-
Access Control: Implement the principle of least privilege, granting users only the access they need to perform their job duties. Regularly review and update access permissions.
-
Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access, even if a breach occurs.
-
Regular Security Audits and Vulnerability Assessments: Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses in your Office365 environment.
-
Threat Detection and Response Systems: Implement advanced threat detection and response systems to quickly identify and respond to potential security incidents.
-
Regular Software Updates and Patching: Keep all software and applications up-to-date with the latest security patches to mitigate known vulnerabilities.
-
Security Information and Event Management (SIEM) Systems: Leverage SIEM systems to monitor and analyze security logs for suspicious activity.
Specific Office365 Security Settings to Implement:
-
Conditional Access Policies: Configure Conditional Access Policies to control access based on user location, device, and other factors. [Link to Microsoft documentation on Conditional Access]
-
Data Loss Prevention (DLP): Implement DLP policies to prevent sensitive data from leaving your organization’s network. [Link to Microsoft documentation on DLP]
-
Advanced Threat Protection (ATP): Utilize Microsoft 365 ATP to protect against advanced threats, including phishing and malware. [Link to Microsoft documentation on ATP]
Conclusion
This shocking case study of an Office365 account compromise underscores the devastating consequences of inadequate cloud security and the critical need for proactive insider threat prevention. Millions were stolen, sensitive data was compromised, and irreparable reputational damage was inflicted, all due to a preventable security lapse. The lessons learned are clear: strong passwords, mandatory MFA, comprehensive cybersecurity awareness training, and regular security audits are not optional – they're essential for protecting your business from Office365 account compromise. Don't become another statistic: Secure your Office365 environment now! Take action today to protect your valuable data and your company's future.

Featured Posts
-
 Persipura Jayapura 8 0 Atas Rans Fc Dominasi Di Playoff Liga 2 Dan Puncak Klasemen Grup K
May 13, 2025
Persipura Jayapura 8 0 Atas Rans Fc Dominasi Di Playoff Liga 2 Dan Puncak Klasemen Grup K
May 13, 2025 -
 The Real Life Men Behind The Great Gatsby Exploring Fitzgeralds Inspirations
May 13, 2025
The Real Life Men Behind The Great Gatsby Exploring Fitzgeralds Inspirations
May 13, 2025 -
 Spor Oko Iz Ava Marinike Tepi Natsionalni Savet Roma Protiv Govora Mrzhnje
May 13, 2025
Spor Oko Iz Ava Marinike Tepi Natsionalni Savet Roma Protiv Govora Mrzhnje
May 13, 2025 -
 Pregnant Cassie Shares Third Babys Gender With Alex Fine
May 13, 2025
Pregnant Cassie Shares Third Babys Gender With Alex Fine
May 13, 2025 -
 Leonardo Di Caprio Hatalmas Gazsija A Mozik Pusztulasa
May 13, 2025
Leonardo Di Caprio Hatalmas Gazsija A Mozik Pusztulasa
May 13, 2025
