Office365 Security Failure Costs Executives Millions

Table of Contents
The High Cost of Data Breaches and Non-Compliance
An Office365 security breach can trigger a cascade of costly consequences. The financial impact extends far beyond the immediate cost of remediation.
Financial Penalties and Legal Fees
Regulatory fines for non-compliance following a data breach can be crippling. Regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) impose hefty penalties for failing to protect personal data. Legal fees for investigations, litigation, and potential class-action lawsuits can further escalate the costs.
- Example 1: In 2021, Company X was fined €20 million for a GDPR violation stemming from an Office365 security failure.
- Example 2: Company Y faced a $5 million settlement in a class-action lawsuit after a data breach exposed customer information stored in their Office365 environment.
Reputational Damage and Loss of Customer Trust
The impact of negative publicity after an Office365 security breach can be devastating. Loss of customer trust translates directly into decreased sales and customer churn, significantly impacting revenue. Repairing a damaged reputation takes time, resources, and a strategic public relations campaign.
- Example 1: Following a high-profile Office365 data breach, Company Z saw a 20% drop in sales within the first quarter.
- Example 2: Company A's stock price plummeted after an Office365 security incident revealed sensitive financial data.
Business Interruption and Operational Downtime
System downtime following an Office365 security breach leads to lost productivity, project delays, and significant operational disruptions. The costs of restoring systems, recovering data, and implementing enhanced security measures can quickly mount.
- Example 1: Company B experienced five days of downtime following a ransomware attack that exploited an Office365 vulnerability, costing them an estimated $1 million in lost revenue.
- Example 2: The recovery process for Company C, after an Office365 security incident, took three months and involved significant IT resources.
Common Office365 Security Vulnerabilities Exploited by Cybercriminals
Understanding the common attack vectors is crucial for building a robust Office365 security posture. Cybercriminals exploit various vulnerabilities to gain access to sensitive data.
Phishing and Social Engineering Attacks
Phishing emails and social engineering tactics remain highly effective in compromising Office365 accounts. These attacks often leverage sophisticated techniques to trick users into revealing their credentials or downloading malicious software. Regular employee security awareness training is paramount.
- Example 1: Spear phishing targeting specific executives within an organization remains a common attack vector.
- Example 2: Malicious links disguised as legitimate Office365 login pages continue to ensnare unsuspecting users.
Weak or Stolen Credentials
Weak passwords and password reuse significantly increase the risk of an Office365 security breach. Implementing multi-factor authentication (MFA) and robust password management practices is crucial.
- Statistic: A significant percentage of data breaches are attributed to weak or stolen credentials.
- Recommendation: Enforce strong password policies and encourage the use of password managers.
Unpatched Software and Outdated Systems
Failing to keep Office365 software and related systems up-to-date with security patches leaves your organization vulnerable to known exploits. Regular updates are essential for patching security vulnerabilities.
- Example 1: The NotPetya ransomware outbreak exploited a vulnerability in outdated versions of Windows.
- Example 2: Many security breaches are caused by neglecting to apply critical security patches promptly.
Shadow IT and Unsecured Third-Party Applications
The use of unauthorized applications and cloud services that integrate with Office365 creates significant security risks. Implement strong access controls and monitor access to third-party applications.
- Example 1: A compromised third-party app with access to Office365 data can lead to a significant data breach.
- Example 2: Shadow IT increases the attack surface and makes it harder to maintain a secure environment.
Proactive Strategies to Mitigate Office365 Security Risks
Proactive security measures are far more cost-effective than reacting to a breach. Implementing robust security strategies is a crucial investment for any business.
Implementing Robust Security Measures
Multi-factor authentication (MFA) is a fundamental security measure. Advanced threat protection (ATP) and data loss prevention (DLP) tools provide enhanced security capabilities.
- Key Feature 1: Enable MFA for all user accounts.
- Key Feature 2: Configure ATP to detect and block malicious emails and attachments.
- Key Feature 3: Utilize DLP policies to prevent sensitive data from leaving your organization.
Regular Security Audits and Penetration Testing
Regular security assessments identify vulnerabilities before they can be exploited. Penetration testing simulates real-world attacks to uncover weaknesses in your security posture.
- Frequency Recommendation: Conduct security audits at least annually, and penetration testing every six months.
Employee Security Awareness Training
Educating employees about phishing scams, social engineering, and password security is crucial. Regular security awareness training programs significantly reduce the risk of human error.
- Effective Method 1: Conduct interactive training sessions.
- Effective Method 2: Use simulated phishing campaigns to test employee awareness.
Conclusion: Protecting Your Business from Costly Office365 Security Failures
Office365 security failures can lead to devastating financial consequences, including hefty fines, legal fees, reputational damage, and business interruption. Proactive measures, including robust security measures, regular security audits, and employee training, are essential to mitigate these risks. Don't let an Office365 security failure cost your business millions. Invest in comprehensive security solutions, including robust password policies, multi-factor authentication, and regular security awareness training, for robust Office365 security and data breach prevention today. Prioritize Office365 security and protect your business from the devastating impact of a cybersecurity incident.

Featured Posts
-
 Connaissez Vous Bien La Loire Atlantique Un Quiz Pour Le Decouvrir
May 22, 2025
Connaissez Vous Bien La Loire Atlantique Un Quiz Pour Le Decouvrir
May 22, 2025 -
 Wyoming Wildlife Needs You Join The Guided Fishing Advisory Board
May 22, 2025
Wyoming Wildlife Needs You Join The Guided Fishing Advisory Board
May 22, 2025 -
 Cest La Petite Italie De L Ouest Architecture Toscane Et Charme Inattendu
May 22, 2025
Cest La Petite Italie De L Ouest Architecture Toscane Et Charme Inattendu
May 22, 2025 -
 Barclay Center Hosts Vybz Kartel Concert This April In Nyc
May 22, 2025
Barclay Center Hosts Vybz Kartel Concert This April In Nyc
May 22, 2025 -
 Reactie Geen Stijl Op Abn Amro Rapport Zijn Nederlandse Huizen Betaalbaar
May 22, 2025
Reactie Geen Stijl Op Abn Amro Rapport Zijn Nederlandse Huizen Betaalbaar
May 22, 2025
Latest Posts
-
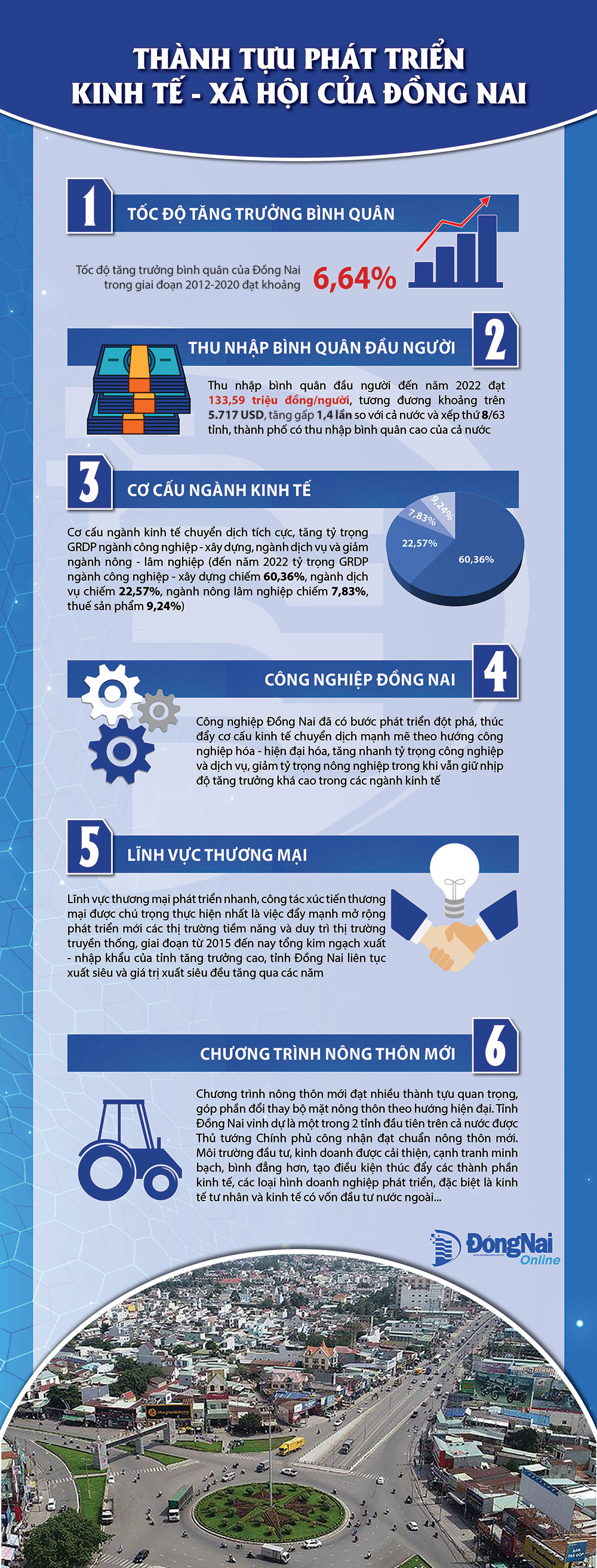 Phan Tich Tac Dong Kinh Te Xa Hoi Cua Cau Ma Da Dong Nai
May 22, 2025
Phan Tich Tac Dong Kinh Te Xa Hoi Cua Cau Ma Da Dong Nai
May 22, 2025 -
 Cau Ma Da Giai Phap Giao Thong Hien Dai Cho Dong Nai
May 22, 2025
Cau Ma Da Giai Phap Giao Thong Hien Dai Cho Dong Nai
May 22, 2025 -
 Xay Dung Cau Ma Da Thuc Day Phat Trien Kinh Te Dong Nai
May 22, 2025
Xay Dung Cau Ma Da Thuc Day Phat Trien Kinh Te Dong Nai
May 22, 2025 -
 Danh Gia Du An Xay Dung Cau Ma Da Dong Nai
May 22, 2025
Danh Gia Du An Xay Dung Cau Ma Da Dong Nai
May 22, 2025 -
 Cau Ma Da Du An Trong Diem Ket Noi Dong Nai
May 22, 2025
Cau Ma Da Du An Trong Diem Ket Noi Dong Nai
May 22, 2025
