The Rise Of Post-Quantum Cryptography: Market Projections And Technological Advancements
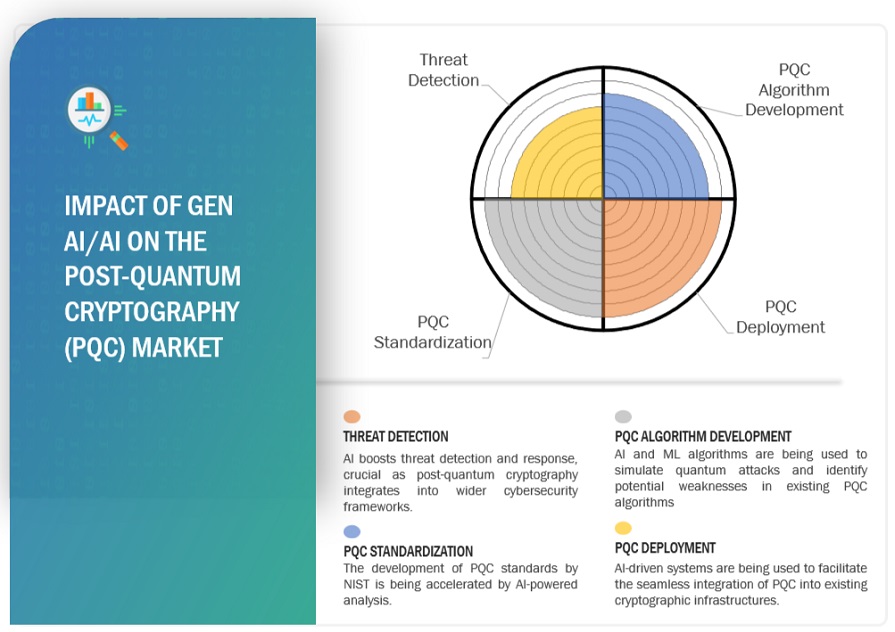
Table of Contents
H2: The Growing Threat of Quantum Computing
Quantum computers, leveraging the principles of quantum mechanics, possess the potential to exponentially outperform classical computers in specific computational tasks. This unparalleled processing power poses a significant threat to currently used public-key cryptography algorithms like RSA and Elliptic Curve Cryptography (ECC), which underpin much of our online security infrastructure. These algorithms, widely used for secure communication, data protection, and digital signatures, are vulnerable to attacks from sufficiently powerful quantum computers.
The timeline for the development of such powerful quantum computers is a subject of ongoing debate, but the consensus among experts is that the threat is real and imminent. Delaying preparation is a risky gamble.
- Vulnerable Encryption Algorithms: RSA, ECC, DSA (Digital Signature Algorithm)
- Potential Consequences of a Quantum Attack: Massive data breaches exposing sensitive personal and financial information, crippling financial systems, compromising national security, and disrupting global supply chains.
- High-Risk Industries: Finance (online banking, payment systems), healthcare (patient data), government (classified information), and defense (military communications).
H2: Understanding Post-Quantum Cryptography (PQC)
Post-Quantum Cryptography encompasses cryptographic algorithms designed to be secure against attacks from both classical and quantum computers. It's a proactive measure to safeguard our digital assets in the era of quantum computing. Several different types of PQC algorithms are currently under development and evaluation:
- Lattice-based cryptography: Relies on the hardness of lattice problems in high-dimensional spaces. Offers strong security and relatively good performance.
- Code-based cryptography: Based on the difficulty of decoding random linear codes. Offers strong security but can be less efficient than lattice-based methods.
- Multivariate cryptography: Uses multivariate polynomial equations over finite fields. Can offer good performance but security considerations are crucial.
- Hash-based cryptography: Utilizes cryptographic hash functions to generate digital signatures. Offers strong security but has limitations on the number of signatures that can be generated.
Bullet points:
- Advantages of PQC Algorithms: Resistance to quantum computer attacks, strong security guarantees, and ongoing research leading to improved efficiency.
- Disadvantages of PQC Algorithms: Some algorithms may have higher computational overhead compared to classical algorithms, and the relatively nascent nature of some PQC methods means ongoing analysis and improvement are needed.
- Standardization Efforts: The National Institute of Standards and Technology (NIST) is leading a crucial standardization effort to select and recommend PQC algorithms for widespread adoption. Other organizations are also contributing to this important work.
- Key Features of PQC Resistance: Mathematical hardness assumptions that are believed to be resistant to attacks by both classical and quantum algorithms.
H2: Market Projections for Post-Quantum Cryptography
The market for Post-Quantum Cryptography is experiencing significant growth, driven by the escalating threat of quantum computing, increasing regulatory pressure, and proactive adoption by forward-thinking organizations. Market research firms predict substantial expansion in the coming years.
- Market Size Projections (5-10 years): While precise figures vary depending on the source, many forecasts indicate substantial market growth, reaching billions of dollars in the next decade.
- Key Market Segments: Software solutions integrating PQC libraries, hardware implementing PQC algorithms (e.g., specialized cryptographic processors), and consulting services to help organizations transition to PQC.
- Geographic Regions: North America and Europe are expected to lead in PQC adoption initially, followed by a rapid expansion in Asia-Pacific and other regions.
H2: Technological Advancements in Post-Quantum Cryptography
Significant progress is being made in PQC research and development. However, challenges remain in implementing and deploying PQC solutions at scale.
- New Algorithms and Performance Improvements: Constant research is yielding new and more efficient PQC algorithms, improving their performance and practicality.
- Advances in Hardware Acceleration: Specialized hardware, such as ASICs (Application-Specific Integrated Circuits) and FPGAs (Field-Programmable Gate Arrays), are crucial for improving the performance of PQC algorithms, making them more suitable for real-world applications.
- Progress towards Standardization and Interoperability: The ongoing NIST standardization process is vital for creating interoperable PQC solutions, promoting wider adoption and preventing fragmentation.
H3: The Role of Hardware Acceleration in PQC Adoption
Hardware acceleration is critical for overcoming performance limitations of some PQC algorithms. Dedicated hardware can significantly reduce the computational overhead, making PQC practical for high-throughput applications like secure communication and data encryption. This includes developments in both general-purpose and application-specific hardware solutions. Examples include specialized processors optimized for specific PQC algorithms, enabling faster encryption and decryption speeds.
3. Conclusion
The growing threat of quantum computing necessitates the adoption of Post-Quantum Cryptography. Market projections indicate a rapidly expanding market for PQC solutions as organizations proactively prepare for this shift. Technological advancements are constantly improving the efficiency and practicality of PQC algorithms, making them more viable for widespread deployment. Embrace the future of cybersecurity with Post-Quantum Cryptography. Invest in Post-Quantum Cryptography solutions today to safeguard your valuable data against the imminent quantum threat. Learn more about PQC and how it can protect your organization by conducting further research or contacting a PQC solutions provider.

Featured Posts
-
 Eurovision 2025 Sissal Er Danmarks Kandidat
May 13, 2025
Eurovision 2025 Sissal Er Danmarks Kandidat
May 13, 2025 -
 The Partynextdoor Tory Lanez Feud An Apology And Its Implications
May 13, 2025
The Partynextdoor Tory Lanez Feud An Apology And Its Implications
May 13, 2025 -
 Landman Season 2 Sam Elliott Cast In New Role Report Confirmed
May 13, 2025
Landman Season 2 Sam Elliott Cast In New Role Report Confirmed
May 13, 2025 -
 From Kamala Harris Influencer To Congressional Candidate Gen Zs Political Rise
May 13, 2025
From Kamala Harris Influencer To Congressional Candidate Gen Zs Political Rise
May 13, 2025 -
 Ncaa Tournament Watch Duke Battle Oregon Live Game Day Details
May 13, 2025
Ncaa Tournament Watch Duke Battle Oregon Live Game Day Details
May 13, 2025
