Block Mirror And The Future Of Internet Access: Examining Trigger Circumvention
Table of Contents
How Block Mirrors Work: Bypassing Geo-Restrictions and Censorship
Understanding the Mechanism of Block Mirrors
Block mirrors act as intermediaries, cleverly redirecting requests for blocked content to unblocked servers. They utilize several techniques to achieve this, often employing a combination of methods for robust circumvention. These include:
- Proxy Servers: These act as intermediaries, masking the user's IP address and forwarding requests to the target website.
- VPN (Virtual Private Network): VPNs create an encrypted tunnel, routing internet traffic through a remote server, effectively hiding the user's location and identity.
- DNS Manipulation: By altering DNS settings, block mirrors can redirect requests to alternative servers hosting copies of the blocked content.
- IP Masking: This technique disguises the user's true IP address, making it appear as though the request originates from a different location.
Accessing blocked content with a block mirror typically involves these steps:
- The user initiates a request to access a blocked website.
- The request is routed through the block mirror's server.
- The block mirror masks the user's IP address and location.
- The request is forwarded to an unblocked server hosting a mirror of the blocked content.
- The content is returned to the user, appearing as if accessed directly.
It's important to differentiate block mirrors from other circumvention methods. While VPNs primarily focus on privacy and security, and Tor emphasizes anonymity, block mirrors are specifically designed to bypass censorship by providing alternative access points to blocked content.
Types of Content Accessed via Block Mirrors
Block mirrors provide access to a wide range of content otherwise restricted by geographical limitations or censorship. This includes:
- Websites: News sites, blogs, and social media platforms banned in certain countries. For example, access to Facebook or Twitter might be blocked in some authoritarian regimes, but block mirrors can help users circumvent these restrictions.
- Streaming Services: Geo-restricted streaming services like Netflix or Hulu offer different content libraries depending on location. Block mirrors can unlock access to content unavailable in a user's region.
- Social Media Platforms: Access to specific social media platforms can be restricted in some countries. Block mirrors can help bypass these restrictions.
- News Sources: Independent news sources critical of a government might be blocked. Block mirrors can restore access to alternative perspectives.
Regions with high censorship, such as China, Iran, and North Korea, frequently see the use of block mirrors to access information otherwise unavailable to their citizens.
Trigger Circumvention and its Effectiveness
Trigger circumvention refers to the techniques employed by block mirrors to avoid detection and blocking by censorship mechanisms. Websites and governments often employ sophisticated methods to identify and block access attempts from block mirrors, including IP address blacklisting, deep packet inspection, and content filtering. Block mirrors combat these techniques through various strategies:
- Dynamic IP Addressing: Constantly changing IP addresses makes it difficult for censors to blacklist them effectively.
- Obfuscation Techniques: Hiding the true nature of the request to avoid detection by censorship filters.
- Multiple Server Locations: Distributing the service across multiple servers in different locations increases resilience against takedowns.
However, the effectiveness of block mirrors is constantly tested by evolving censorship techniques. The ongoing "cat and mouse" game between censorship and circumvention technology means that the effectiveness of a block mirror can fluctuate.
The Ethical and Legal Implications of Using Block Mirrors
Ethical Considerations
The use of block mirrors raises several ethical questions:
- Copyright Infringement: Accessing copyrighted material through a block mirror, without proper authorization, is illegal in many jurisdictions.
- Malicious Use: Block mirrors could be used for malicious purposes, such as accessing and distributing illegal content or engaging in cybercrime.
- Privacy Concerns: While some block mirrors prioritize user privacy, others may collect and sell user data, raising concerns about online surveillance.
- Internet Freedom vs. Regulation: The debate continues regarding the balance between internet freedom and the need for regulations to prevent misuse of circumvention tools.
Legal Ramifications
The legal status of using block mirrors varies significantly across jurisdictions.
- Copyright Violations: Downloading or streaming copyrighted content without permission through a block mirror can lead to severe legal consequences, including fines and lawsuits.
- Accessing Prohibited Content: Accessing content deemed illegal or harmful in a specific region can result in legal repercussions, ranging from warnings to imprisonment.
- Evolving Legal Landscape: The legal framework surrounding internet censorship and circumvention technologies is constantly evolving, making it challenging to keep up with the changing regulations.
The Future of Block Mirrors and Internet Access
Technological Advancements and their Impact
Advancements in technology will significantly impact both the effectiveness of block mirrors and the sophistication of censorship mechanisms.
- AI-Powered Censorship: Artificial intelligence is increasingly used to detect and block circumvention attempts, requiring block mirrors to adapt with more advanced techniques.
- Enhanced Deep Packet Inspection: More sophisticated deep packet inspection methods can identify and block encrypted traffic, reducing the effectiveness of VPNs and other circumvention tools.
- New Circumvention Technologies: The development of decentralized and resilient network architectures, such as blockchain-based solutions, could offer new avenues for internet access.
The Ongoing Battle for Internet Freedom
Block mirrors play a crucial role in the fight for internet freedom and access to information.
- Political Activism: Block mirrors enable activists and journalists in repressive regimes to access information and communicate freely, bypassing censorship.
- Social Movements: They facilitate the organization and communication of social movements, allowing for the free exchange of ideas and mobilization.
- Long-Term Implications: The ongoing development and use of block mirrors will continue to shape the dynamics between internet freedom and government control.
Conclusion: The Enduring Relevance of Block Mirrors in the Digital Age
Block mirrors represent a significant technological development in the ongoing struggle for unrestricted internet access. Their functionality, while technically sophisticated, is ethically and legally complex. Understanding the mechanisms of block mirrors, their potential for both positive and negative use, and the evolving legal landscape surrounding their use is crucial. While their effectiveness against increasingly sophisticated censorship methods remains a challenge, their role in enabling access to information in restricted environments highlights their enduring relevance in the digital age. Learn more about block mirror technology, explore the implications of block mirror use, and understand the challenges of internet censorship and block mirror solutions. The future of internet access depends, in part, on the continued development and responsible use of these technologies.

Featured Posts
-
 Jalen Brunson The Face Of Liberty A Knicks Fans Bold Petition
May 16, 2025
Jalen Brunson The Face Of Liberty A Knicks Fans Bold Petition
May 16, 2025 -
 In Quale Acqua Troviamo Piu Microplastiche
May 16, 2025
In Quale Acqua Troviamo Piu Microplastiche
May 16, 2025 -
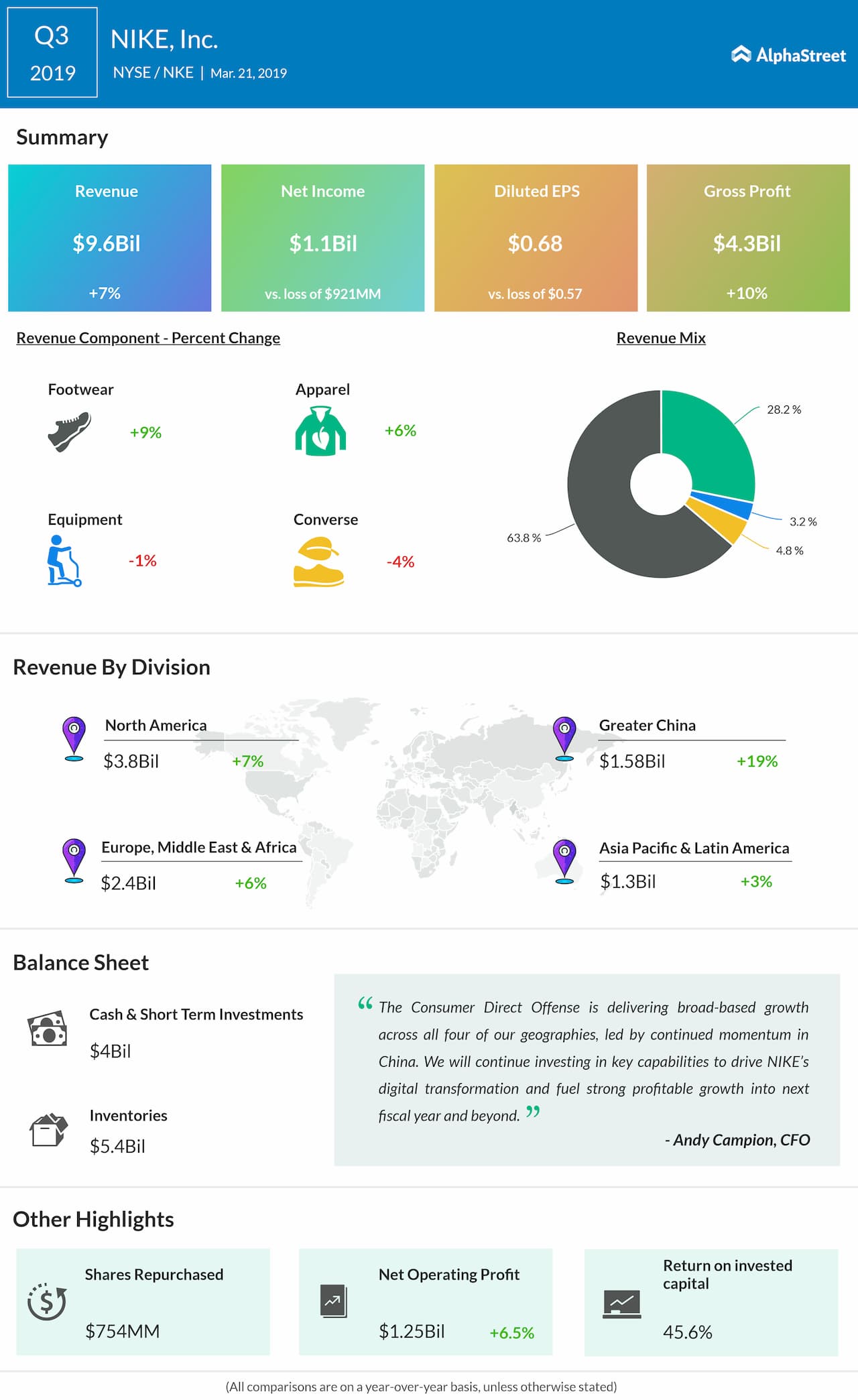 Nike Q3 Earnings Jefferies Warns Of Impact On Foot Lockers Short Term Performance
May 16, 2025
Nike Q3 Earnings Jefferies Warns Of Impact On Foot Lockers Short Term Performance
May 16, 2025 -
 Jalen Brunsons Return Knicks Pistons Playoff Push
May 16, 2025
Jalen Brunsons Return Knicks Pistons Playoff Push
May 16, 2025 -
 Knicks Fans Petition Replace Lady Libertys Face With Jalen Brunson
May 16, 2025
Knicks Fans Petition Replace Lady Libertys Face With Jalen Brunson
May 16, 2025
