Federal Investigation: Millions Stolen Via Office365 Executive Hacks

Table of Contents
The Modus Operandi: How the Office365 Executive Hacks Occurred
The Office365 executive hacks leveraged a multi-pronged approach, combining sophisticated social engineering with technical exploits. The attackers focused on high-value targets – executives with access to significant financial resources and authority. This approach, often referred to as CEO fraud or Business Email Compromise (BEC), relies on deception and manipulation rather than brute-force attacks.
- Spear Phishing: Highly targeted spear phishing campaigns were deployed, using emails tailored to individual executives. These emails often mimicked legitimate communications, creating a sense of urgency and trust.
- Social Engineering: Attackers employed sophisticated social engineering techniques to gain the trust of executives, often exploiting existing relationships or creating believable scenarios.
- Credential Harvesting: Once trust was established, the attackers used various methods to harvest credentials, including malicious links, attachments containing malware, or even direct requests for login details.
- Bypassing Multi-Factor Authentication (MFA): MFA, while a crucial security layer, was bypassed in several cases. This suggests the attackers utilized techniques like SIM swapping, exploiting weak MFA implementations, or compromising secondary authentication devices.
- Fund Transfer: After gaining access, the attackers swiftly transferred funds through fraudulent wire transfers and manipulated invoices, often targeting accounts payable departments.
The Scale of the Damage: Millions Lost and the Impact on Businesses
The financial losses resulting from these Office365 executive hacks are staggering. While precise figures remain confidential during the ongoing federal investigation, estimates suggest millions of dollars were stolen across multiple victim organizations. The impact extends far beyond immediate financial losses:
- Financial Losses: Millions of dollars lost directly through fraudulent wire transfers and altered payments. This can cripple small to medium-sized businesses and significantly impact the bottom line of larger corporations.
- Reputational Damage: Data breaches and financial fraud severely damage an organization's reputation and erode investor confidence. This can lead to decreased stock prices, loss of clients, and difficulty attracting new business.
- Regulatory Penalties: Organizations may face substantial regulatory fines and legal repercussions for failing to adequately protect sensitive data and prevent financial fraud. Compliance violations can trigger significant penalties under various data protection and financial regulations.
- Data Loss: Beyond financial losses, the compromise of executive accounts often leads to the loss of sensitive company data, including intellectual property, strategic plans, and customer information. This data loss can have long-term consequences.
The Federal Investigation: Current Status and Potential Outcomes
A multi-agency federal investigation, likely involving the FBI and potentially the Secret Service, is currently underway. The investigation is focused on identifying the perpetrators, tracing the stolen funds, and bringing those responsible to justice.
- FBI Investigation: The FBI's cybercrime division is likely leading the investigation, utilizing its expertise in tracking down cybercriminals and recovering stolen assets.
- International Cooperation: Given the global nature of cybercrime, international cooperation with law enforcement agencies in other countries will likely be crucial in apprehending the perpetrators.
- Criminal Charges: Those responsible will likely face significant criminal charges, including wire fraud, identity theft, and computer intrusion, leading to substantial prison sentences and fines.
- Cyber Security Legislation: This incident may accelerate the development and implementation of stricter cybersecurity legislation and regulations aimed at preventing similar attacks.
Protecting Your Organization: Best Practices to Prevent Office365 Executive Hacks
Preventing Office365 executive hacks requires a multi-layered approach focused on both technical security and employee awareness.
- Robust Multi-Factor Authentication (MFA): Implement and rigorously enforce MFA for all accounts, especially executive-level accounts. This adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Security Awareness Training: Regular, comprehensive security awareness training is essential. Employees should be educated about phishing scams, social engineering tactics, and the importance of secure password management.
- Phishing Simulations: Conduct regular phishing simulations to assess employee awareness and identify vulnerabilities in your security protocols. This allows for proactive remediation of weaknesses.
- Data Loss Prevention (DLP): Implement robust DLP measures to monitor and control the flow of sensitive data within your organization. This helps prevent data exfiltration even if an account is compromised.
- Access Controls: Review and restrict access privileges to sensitive systems and data based on the principle of least privilege. Limit the number of users with access to critical financial systems.
- Threat Intelligence: Leverage threat intelligence feeds to stay informed about emerging threats and vulnerabilities. This allows for proactive security measures and rapid response to potential attacks.
Conclusion
This federal investigation into millions stolen via Office365 executive hacks underscores the critical need for robust cybersecurity measures. The sophistication of these attacks highlights the vulnerability of even seemingly secure systems. Don't become another victim. Strengthen your organization's defenses against Office365 executive hacks by implementing comprehensive security protocols, including strong MFA, regular security awareness training, and proactive threat monitoring. Take control of your cybersecurity now and protect your valuable assets.

Featured Posts
-
 Coordinating Repatriation South Sudan And The Us Government Collaborate
Apr 22, 2025
Coordinating Repatriation South Sudan And The Us Government Collaborate
Apr 22, 2025 -
 5 Essential Dos And Don Ts Succeeding In The Private Credit Market
Apr 22, 2025
5 Essential Dos And Don Ts Succeeding In The Private Credit Market
Apr 22, 2025 -
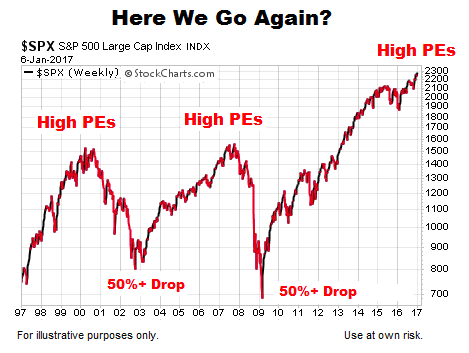 Why Investors Shouldnt Fear High Stock Market Valuations Bof As Perspective
Apr 22, 2025
Why Investors Shouldnt Fear High Stock Market Valuations Bof As Perspective
Apr 22, 2025 -
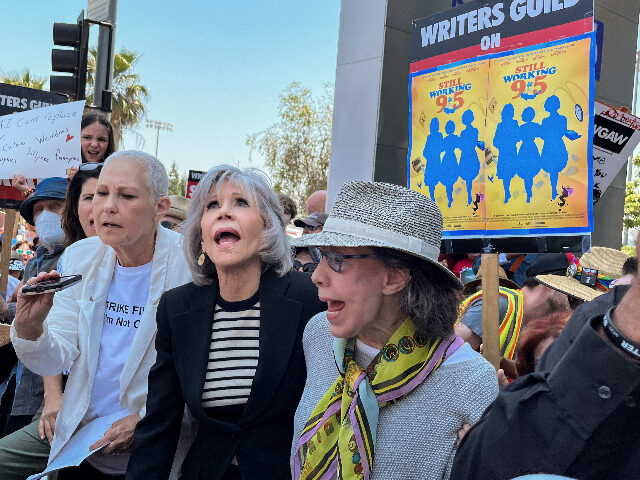 Actors And Writers Strike Hollywood Faces Unprecedented Production Halt
Apr 22, 2025
Actors And Writers Strike Hollywood Faces Unprecedented Production Halt
Apr 22, 2025 -
 Increased Tensions Lead To 1 Billion Funding Cut For Harvard From Trump Administration
Apr 22, 2025
Increased Tensions Lead To 1 Billion Funding Cut For Harvard From Trump Administration
Apr 22, 2025
Latest Posts
-
 Changes To Uk Visa Regulations Addressing Work And Student Visa Misuse
May 10, 2025
Changes To Uk Visa Regulations Addressing Work And Student Visa Misuse
May 10, 2025 -
 Japa New Uk Visa Regulations For Nigerian And Pakistani Nationals
May 10, 2025
Japa New Uk Visa Regulations For Nigerian And Pakistani Nationals
May 10, 2025 -
 Uk Visa Restrictions Report Reveals Potential Nationality Limits
May 10, 2025
Uk Visa Restrictions Report Reveals Potential Nationality Limits
May 10, 2025 -
 Changes To Uk Visa Policy Implications For Nigerians And Pakistanis
May 10, 2025
Changes To Uk Visa Policy Implications For Nigerians And Pakistanis
May 10, 2025 -
 Uk Visa Policy Changes Impact On Nigerian And International Applicants
May 10, 2025
Uk Visa Policy Changes Impact On Nigerian And International Applicants
May 10, 2025
