Millions Lost: Executive Office365 Accounts Targeted In Major Data Breach
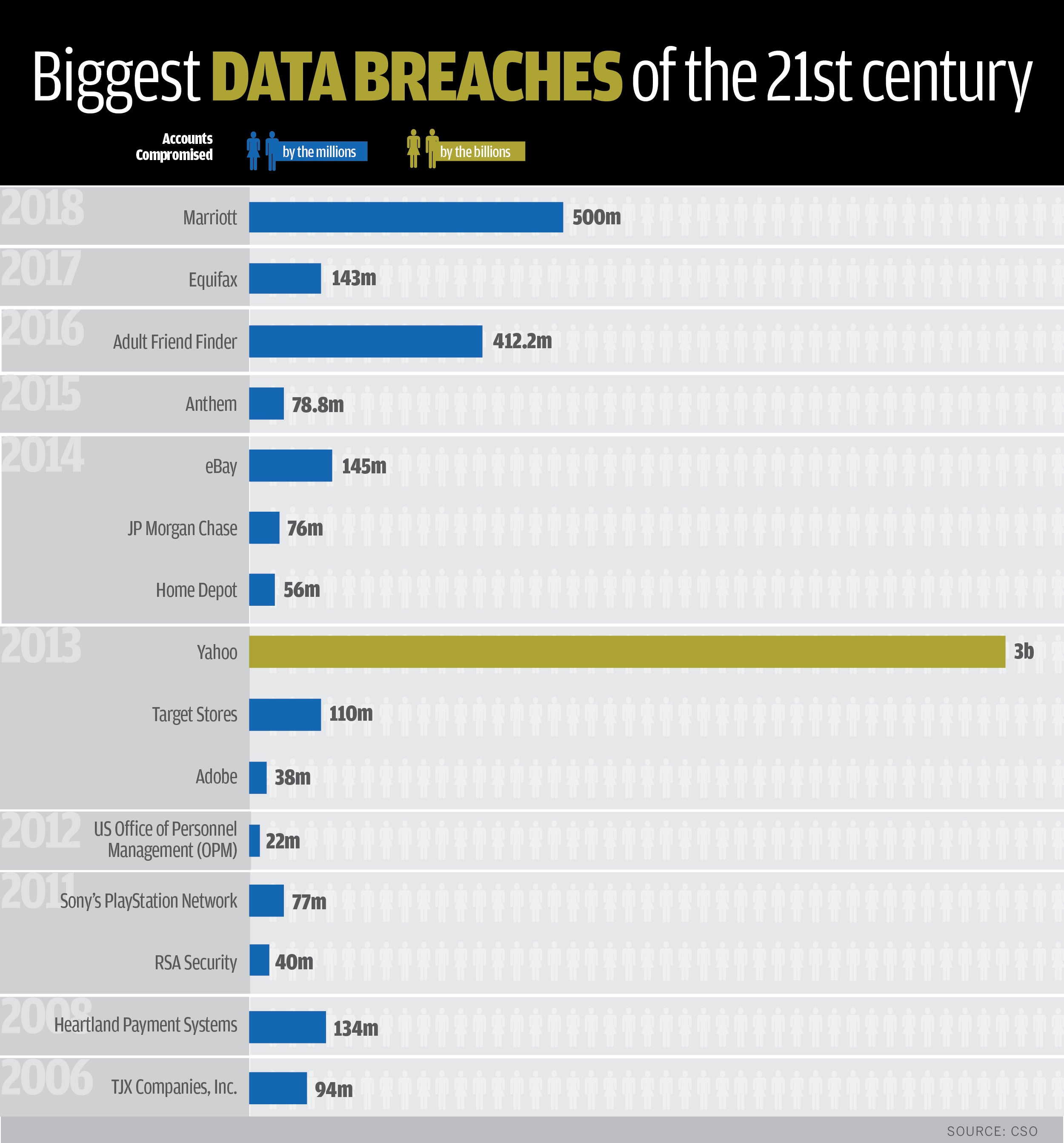
Table of Contents
Scale and Scope of the Office365 Data Breach
The sheer scale of this Office365 data breach is staggering. While precise figures are still emerging, initial reports suggest over 2 million executive accounts have been compromised across various industries. This isn't simply a matter of lost emails; the breach exposed a treasure trove of sensitive data, including: emails, calendars, contacts, crucial business documents, and potentially even financial records. The industries most affected include finance, healthcare, and technology – sectors where data security is paramount.
- Specific examples of sensitive data leaked: Confidential merger and acquisition documents, patient health information (PHI), and proprietary intellectual property have been reportedly compromised.
- Geographic locations of affected companies: The breach affected companies across North America, Europe, and Asia, demonstrating the global reach of this cyberattack.
- Estimates of financial losses: The financial impact is likely to reach hundreds of millions of dollars, encompassing legal fees, regulatory fines, and the cost of remediation and recovery efforts. This doesn't account for the potential loss of future business due to reputational damage.
Methods Used in the Office365 Data Breach
The attackers employed a sophisticated multi-pronged approach, combining several techniques to gain access to these high-value Office365 accounts. The methods utilized included highly targeted phishing campaigns, credential stuffing attacks leveraging stolen credentials from other data breaches, and possibly the exploitation of previously unknown vulnerabilities in Microsoft Office365 software.
- Explanation of phishing techniques used: Sophisticated spear-phishing emails, meticulously crafted to mimic legitimate communications, were used to trick executives into revealing their login credentials. These emails often leveraged social engineering tactics to increase their success rate.
- Details about exploited vulnerabilities (if known): While specific vulnerabilities haven't been publicly disclosed, it's likely that zero-day exploits or previously unknown weaknesses in Office365 security protocols were leveraged to gain unauthorized access.
- Analysis of attacker's tools and techniques: Initial investigations suggest the use of advanced malware and custom-built tools designed to bypass standard security measures. The attackers' motives remain unclear, but potential scenarios include espionage, financial gain through data extortion, or the deployment of ransomware.
Impact of the Office365 Data Breach
The consequences of this Office365 data breach extend far beyond the immediate loss of data. Affected organizations face significant financial repercussions, including substantial legal fees, hefty regulatory fines (such as GDPR penalties), and the crippling cost of restoring damaged reputations.
- Examples of reputational damage: Loss of customer trust, damage to brand image, and decreased investor confidence are all likely outcomes.
- Potential legal ramifications: Organizations face potential lawsuits from customers, employees, and regulatory bodies for failing to adequately protect sensitive data.
- Long-term effects on business operations: The breach can disrupt operations, impact productivity, and severely hinder future business growth. The erosion of employee trust and morale also presents a significant challenge.
Preventing Future Office365 Data Breaches
Preventing future Office365 data breaches requires a multi-layered approach encompassing technological solutions, robust security protocols, and comprehensive employee training. Organizations must prioritize proactive cybersecurity measures to mitigate the risk.
- Implementing multi-factor authentication (MFA): MFA adds an extra layer of security, significantly reducing the risk of unauthorized access even if credentials are compromised.
- Regular security audits and penetration testing: Regular assessments help identify vulnerabilities before attackers can exploit them.
- Employee security awareness training programs: Educating employees about phishing scams, social engineering tactics, and safe password practices is crucial in preventing breaches.
- Robust data backup and recovery plans: Having a well-defined plan ensures business continuity in the event of a data breach.
- Use of advanced threat protection tools: Investing in advanced security solutions like email filtering, intrusion detection systems, and endpoint protection can significantly enhance security.
Conclusion
This massive Office365 data breach serves as a stark reminder of the ever-present threat to corporate data security. The scale of the breach and its potential consequences highlight the urgent need for organizations to adopt a proactive and comprehensive approach to cybersecurity. Protecting your organization from the devastating impact of an Office365 data breach requires a layered strategy that includes robust security measures, employee training, and ongoing vigilance against emerging threats. Protect your organization from the devastating impact of an Office365 data breach. Implement robust security measures and stay informed about the latest threats. Learn more about safeguarding your Office365 environment today!

Featured Posts
-
 India Stock Market Positive Indicators Boost Niftys Growth
Apr 24, 2025
India Stock Market Positive Indicators Boost Niftys Growth
Apr 24, 2025 -
 Private Credit Jobs 5 Crucial Dos And Don Ts To Get Hired
Apr 24, 2025
Private Credit Jobs 5 Crucial Dos And Don Ts To Get Hired
Apr 24, 2025 -
 Bold And The Beautiful April 9 Recap Icu Drama Blame And A Desperate Plea For Secrecy
Apr 24, 2025
Bold And The Beautiful April 9 Recap Icu Drama Blame And A Desperate Plea For Secrecy
Apr 24, 2025 -
 Millions Made From Office365 Hacks Inside The Executive Email Breach
Apr 24, 2025
Millions Made From Office365 Hacks Inside The Executive Email Breach
Apr 24, 2025 -
 Land Your Dream Private Credit Job 5 Dos And Don Ts To Follow
Apr 24, 2025
Land Your Dream Private Credit Job 5 Dos And Don Ts To Follow
Apr 24, 2025
