$16 Million Fine For T-Mobile: Details Of Three Years Of Data Breaches
Table of Contents
The Scope of T-Mobile's Data Breaches: Three Years of Vulnerabilities
The T-Mobile data breaches weren't a single event but rather a series of incidents occurring over three years, showcasing a pattern of vulnerabilities within their systems. Understanding the timeline and the types of data compromised is crucial to grasping the severity of the situation.
Timeline of Events:
While precise dates for each breach may vary depending on the source, the breaches involved a pattern of unauthorized access to sensitive customer data. The timeline revealed a failure to adequately address vulnerabilities in a timely manner.
-
[Insert Date Range for Breach 1]: This breach involved the compromise of [Number] customer accounts, impacting data such as names, addresses, phone numbers, and potentially Social Security numbers. The vulnerability exploited was [Specify vulnerability, e.g., a weakness in a specific software application].
-
[Insert Date Range for Breach 2]: A second breach affected [Number] customers, with compromised data including [Specify data types, e.g., financial information, driver’s license numbers, credit card information]. This breach was reportedly linked to [Specify vulnerability or attack vector, e.g., a phishing campaign].
-
[Insert Date Range for Breach 3]: This incident resulted in the exposure of [Number] customer records, encompassing [Specify data types, e.g., location data, IMEI numbers, account information]. The vulnerability was identified as [Specify vulnerability, e.g., an unpatched server].
Types of Data Compromised:
The breaches exposed a wide array of sensitive personal and financial information, putting customers at significant risk.
-
Personally Identifiable Information (PII): This includes names, addresses, phone numbers, email addresses, dates of birth, and Social Security numbers. The exposure of PII can lead to identity theft and fraud.
-
Financial Data: Compromised financial data, such as credit card numbers, bank account details, and payment information, can result in significant financial losses for affected individuals.
-
Location Data: Exposure of location data could allow attackers to track individuals' movements, potentially leading to stalking or other harmful activities.
-
Account Information: Account usernames, passwords, and other account details were also compromised, enabling unauthorized access to customer accounts.
The severity of each data type's exposure is high, given the potential for identity theft, financial fraud, and other forms of harm. This underscores the critical need for robust security measures.
Regulatory Response and the $16 Million Fine
The T-Mobile data breaches triggered investigations by various regulatory bodies, ultimately leading to a significant financial penalty.
Investigations and Legal Actions:
Following the breaches, regulatory bodies such as the Federal Trade Commission (FTC) and possibly state attorneys general launched investigations. These investigations focused on determining the extent of the breaches, identifying vulnerabilities, and assessing T-Mobile's compliance with relevant data privacy laws, such as the California Consumer Privacy Act (CCPA). The $16 million fine reflects the severity of the violations and the potential harm caused to consumers. Other penalties, such as mandated security improvements, may also have been imposed.
T-Mobile's Response to the Breaches:
T-Mobile issued official statements acknowledging the breaches and outlining steps taken to address the vulnerabilities and mitigate the impact on customers. These measures may have included:
- Notification of affected customers.
- Offering credit monitoring services.
- Implementing improved security protocols.
However, the effectiveness of T-Mobile's response is debatable, given the persistent nature of the breaches over a three-year period. The significant fine suggests that their initial responses were insufficient to prevent further incidents and address the underlying vulnerabilities.
Impact on Consumers and the Broader Implications
The T-Mobile data breaches had a profound impact on millions of consumers, creating significant concerns and risks.
Consumer Concerns and Risks:
Affected consumers faced a heightened risk of:
- Identity theft: The compromise of PII increases the likelihood of identity theft, leading to financial and emotional distress.
- Financial fraud: Access to financial data can enable fraudsters to make unauthorized transactions.
- Account takeover: Compromised account credentials can result in the unauthorized access and manipulation of customer accounts.
Consumers can mitigate these risks by taking proactive steps, including:
- Monitoring credit reports: Regularly check for suspicious activity on credit reports.
- Setting up fraud alerts: Enable fraud alerts with credit bureaus to be notified of potential fraudulent activity.
- Changing passwords: Update passwords for all affected online accounts.
The Bigger Picture: Data Security Best Practices:
The T-Mobile data breaches highlight the critical need for robust data security measures within the telecommunications industry and across all sectors handling sensitive personal data. Proactive cybersecurity strategies, including regular security audits, vulnerability assessments, employee training, and robust incident response plans are crucial. Adherence to industry standards and regulations, such as the NIST Cybersecurity Framework, is paramount.
Conclusion: Learning from T-Mobile's $16 Million Data Breach Fine
T-Mobile's $16 million data breach fine serves as a stark reminder of the significant consequences of inadequate data security. The breaches spanned three years, exposing millions of customers' sensitive information and leading to substantial regulatory action. The incident underscores the importance of prioritizing data security and implementing robust cybersecurity measures to protect consumer privacy. Stay informed about T-Mobile data breach updates and ensure you understand the importance of protecting your personal data. If you believe your information has been compromised, report the breach to the appropriate authorities and consider taking steps to mitigate the risks. Resources for reporting data breaches and obtaining assistance with identity theft are readily available online. Proactive data security measures are not just a best practice; they are a necessity in today's digital landscape.

Featured Posts
-
 Stock Market Rally Nasdaq S And P 500 Gains On Tariff Hopes Live Updates
Apr 24, 2025
Stock Market Rally Nasdaq S And P 500 Gains On Tariff Hopes Live Updates
Apr 24, 2025 -
 Nba All Star Game 2024 Notable Additions To The Festivities Include Green Moody And Hield
Apr 24, 2025
Nba All Star Game 2024 Notable Additions To The Festivities Include Green Moody And Hield
Apr 24, 2025 -
 Alcons 417 5 Million Acquisition Of Village Roadshow Stalking Horse Bid Successful
Apr 24, 2025
Alcons 417 5 Million Acquisition Of Village Roadshow Stalking Horse Bid Successful
Apr 24, 2025 -
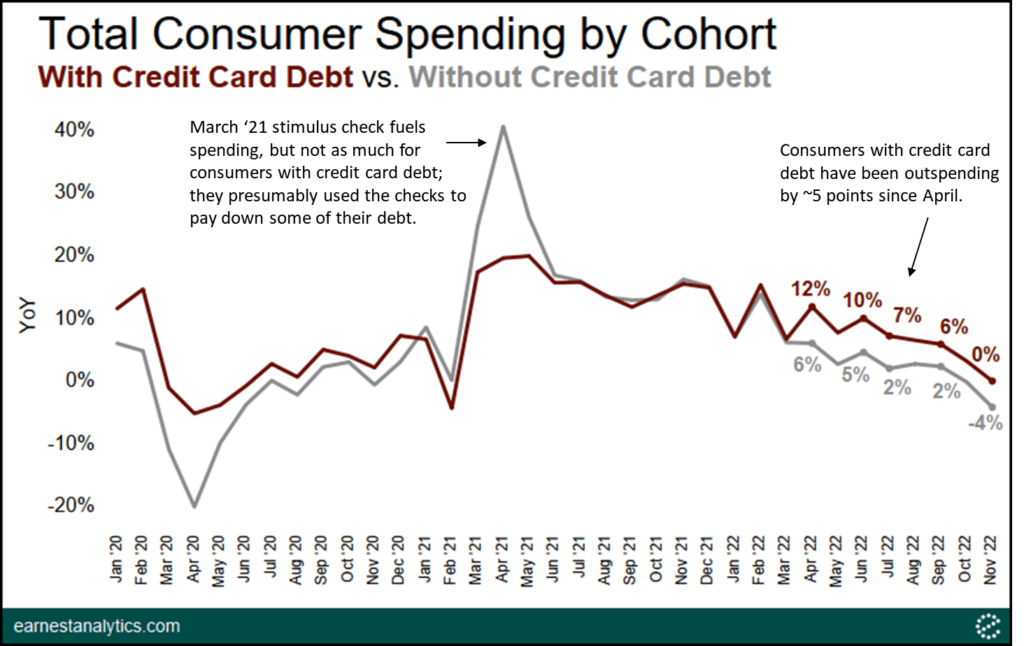 Credit Card Industry Faces Headwinds Amidst Reduced Consumer Spending
Apr 24, 2025
Credit Card Industry Faces Headwinds Amidst Reduced Consumer Spending
Apr 24, 2025 -
 Canadian Auto Industry Fights Back A Five Point Plan To Counter Us Trade War
Apr 24, 2025
Canadian Auto Industry Fights Back A Five Point Plan To Counter Us Trade War
Apr 24, 2025
