Cybercriminal Profits From Executive Office365 Account Compromise
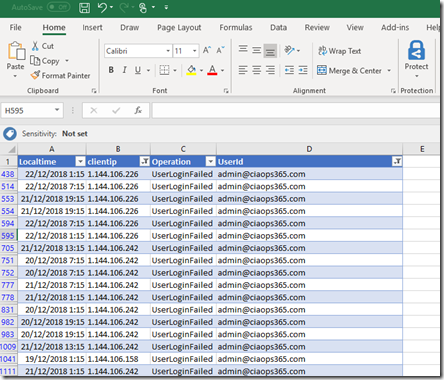
Table of Contents
Methods of Executive Office365 Account Compromise
Cybercriminals employ sophisticated techniques to compromise executive Office365 accounts. These attacks often leverage the perceived trust and authority associated with high-level executives.
Phishing and Spear Phishing Attacks
Phishing and spear phishing attacks are common entry points. Phishing campaigns use generic emails attempting to trick recipients into revealing sensitive information. Spear phishing attacks, however, are far more targeted. They utilize personalized emails, often mimicking legitimate communications from known contacts or organizations, leveraging current events or internal company information to increase their success rate.
- Examples of sophisticated phishing emails: Emails disguised as urgent payment requests, fake invoices, or notifications from seemingly legitimate services.
- Use of social engineering: Manipulating the recipient's psychology to induce a sense of urgency or fear, exploiting their trust to gain access to credentials.
- Targeting vulnerabilities in executive decision-making: Exploiting the executive's busy schedule and the pressure to make quick decisions to bypass security protocols.
- Keyword integration: Phishing campaigns, spear phishing attacks, social engineering, email security, CEO fraud.
Credential Stuffing and Brute-Force Attacks
These automated attacks leverage lists of stolen usernames and passwords (credential stuffing) or systematically try various password combinations (brute-force attacks) to gain unauthorized access. These methods exploit weak passwords or passwords reused across multiple platforms.
- How these attacks work: Credential stuffing uses previously compromised credentials; brute-force attacks use algorithms to try numerous password variations.
- Why strong, unique passwords are crucial: Using strong, unique passwords for each account significantly reduces vulnerability to these attacks.
- Importance of multi-factor authentication (MFA): Implementing MFA adds an extra layer of security, making it exponentially more difficult for attackers to gain access even if they obtain the password.
- Keyword integration: Credential stuffing, brute force attacks, password security, MFA, multi-factor authentication, password manager.
Exploiting Software Vulnerabilities
Outdated software and unpatched vulnerabilities provide easy access for cybercriminals. Exploiting these weaknesses often requires minimal technical expertise.
- Importance of regular software updates: Keeping all software updated with the latest security patches is critical to prevent exploitation.
- Vulnerability scanning: Regular vulnerability scans identify potential weaknesses that need to be addressed.
- Patch management: A robust patch management system ensures timely deployment of security updates.
- Keyword integration: Software vulnerabilities, patch management, security updates, vulnerability scanning, zero-day exploit.
Profiting from Compromised Accounts
Once access is gained, cybercriminals can profit in several ways.
Financial Theft and Ransomware
Financial theft is a primary motive. Cybercriminals may initiate fraudulent wire transfers, manipulate accounting systems, or deploy ransomware to encrypt sensitive data and demand a ransom for its release.
- Examples of financial fraud schemes: Diverting funds to offshore accounts, creating fake invoices, manipulating expense reports.
- How ransomware operates: Ransomware encrypts data, making it inaccessible until a ransom is paid.
- The high costs of paying ransoms: Paying ransoms doesn't guarantee data recovery and often emboldens attackers.
- Keyword integration: Financial fraud, ransomware attacks, data encryption, ransom demands, data recovery.
Data Exfiltration and Insider Trading
Stolen data, including sensitive corporate information, intellectual property, or customer data, can be sold on the dark web or used for insider trading.
- The value of sensitive corporate data: Corporate secrets, customer lists, and intellectual property are highly valuable commodities on the dark web.
- The risks of data breaches: Data breaches can lead to significant financial losses, legal repercussions, and reputational damage.
- Examples of insider trading schemes: Using stolen information to make profitable trades before public announcements.
- Keyword integration: Data exfiltration, dark web, insider trading, data breach consequences, data loss prevention.
Business Email Compromise (BEC)
BEC attacks involve impersonating executives to conduct fraudulent transactions or steal intellectual property.
- Examples of BEC schemes: Requesting fraudulent wire transfers, soliciting confidential information, or compromising sensitive projects.
- How to identify fraudulent emails: Verify requests through multiple communication channels and be wary of unusual urgency or requests outside normal procedures.
- The importance of verification procedures: Strict verification protocols are essential to prevent BEC attacks.
- Keyword integration: Business Email Compromise (BEC), email fraud, impersonation attacks, verification procedures, email authentication.
Protecting Against Executive Office365 Account Compromise
Proactive measures are vital to prevent executive Office365 account compromises.
Implementing Robust Security Measures
Strong security practices form the first line of defense.
- Best practices for password management: Implement strong, unique passwords, utilize a password manager, and enforce regular password changes.
- MFA options: Utilize multi-factor authentication for all accounts, including Office365.
- Types of security awareness training: Regular training for employees on phishing recognition and safe internet practices.
- Importance of regular security assessments: Conduct regular security audits and penetration testing to identify vulnerabilities.
- Keyword integration: Security awareness training, multi-factor authentication, password management, security audit, cybersecurity best practices, security awareness training.
Utilizing Advanced Threat Protection
Advanced threat protection tools provide an additional layer of security.
- Examples of advanced threat protection features: Real-time malware detection, email filtering, anomaly detection.
- Benefits of using such tools: Enhanced email security, reduced risk of successful attacks, improved overall security posture.
- How they enhance security posture: Advanced threat protection significantly reduces the likelihood of successful cyberattacks.
- Keyword integration: Advanced threat protection, email security solutions, threat detection, security information and event management (SIEM), cybersecurity solutions.
Conclusion
Cybercriminals profit handsomely from compromised executive Office365 accounts through various methods, resulting in significant financial losses, reputational damage, and legal repercussions. Implementing robust security measures, including strong passwords, multi-factor authentication, security awareness training, and advanced threat protection, is paramount. Regular security audits and vulnerability scanning are also crucial. Failure to take proactive steps leaves your organization vulnerable to these costly attacks. Protect Your Executives Today by implementing comprehensive cybersecurity solutions and securing your Office365 accounts now. Learn more about preventing executive Office365 compromise and safeguarding your organization's future.

Featured Posts
-
 Lewis Hamilton Mercedes Investigation Following New Information
May 26, 2025
Lewis Hamilton Mercedes Investigation Following New Information
May 26, 2025 -
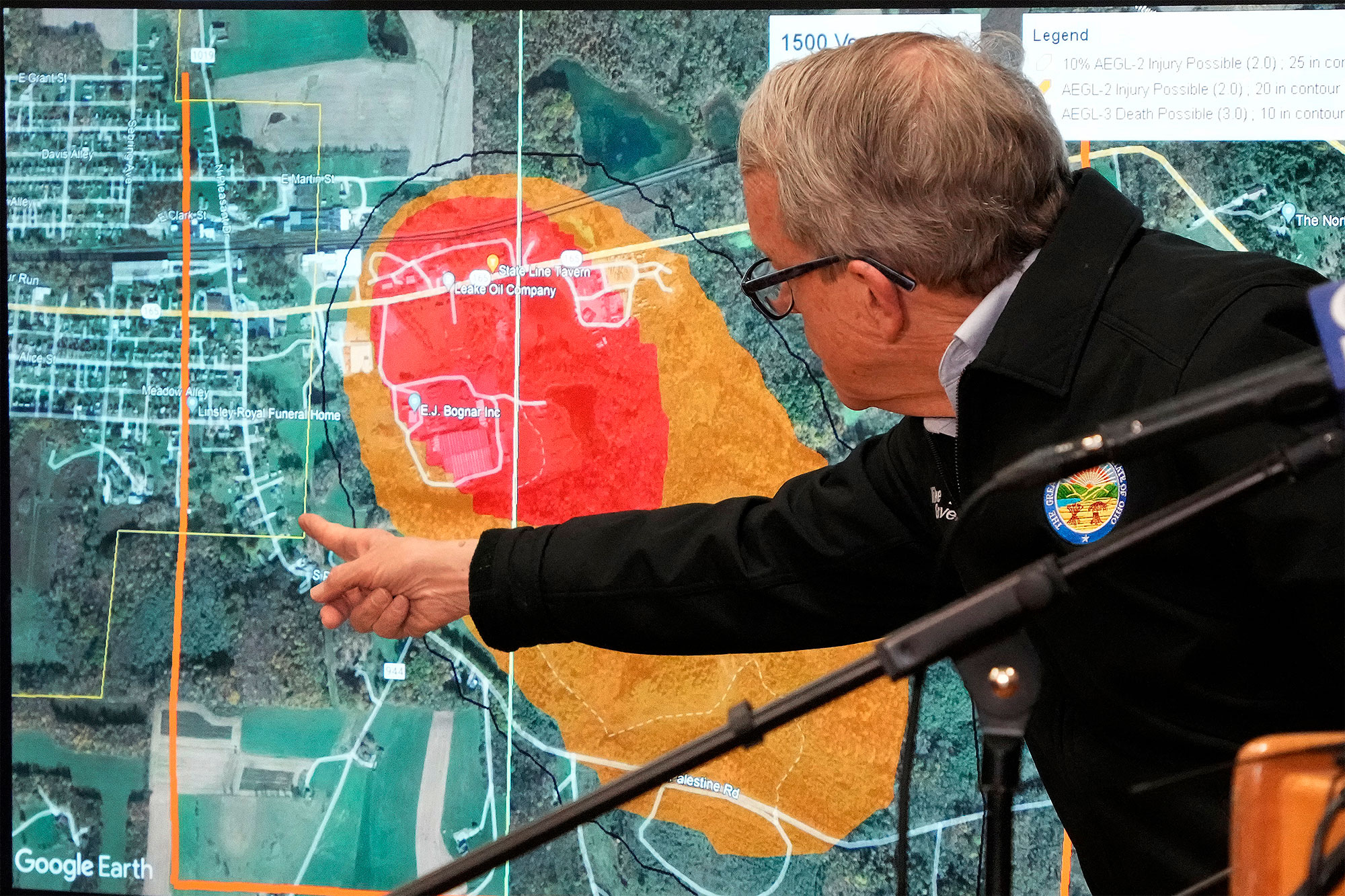 Investigation Into Toxic Chemical Persistence Following Ohio Train Derailment
May 26, 2025
Investigation Into Toxic Chemical Persistence Following Ohio Train Derailment
May 26, 2025 -
 Jadwal Siaran Langsung Moto Gp Argentina 2025 Di Trans7 Saksikan Balapan Seru
May 26, 2025
Jadwal Siaran Langsung Moto Gp Argentina 2025 Di Trans7 Saksikan Balapan Seru
May 26, 2025 -
 A Fathers Love Jonathan Peretz Holds His Son After A Year Of Loss
May 26, 2025
A Fathers Love Jonathan Peretz Holds His Son After A Year Of Loss
May 26, 2025 -
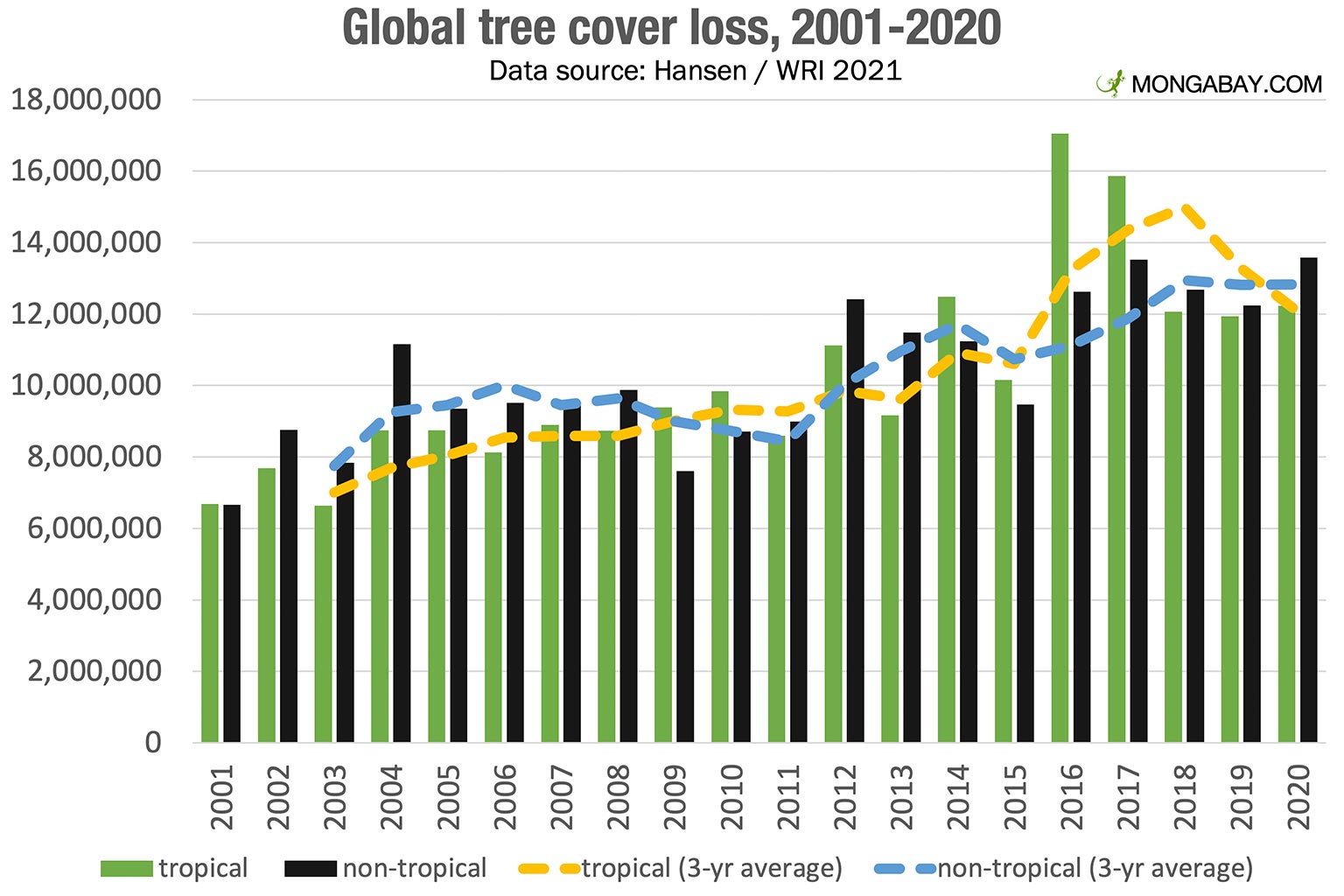 Wildfires Intensify Global Forest Loss A Record Breaking Crisis
May 26, 2025
Wildfires Intensify Global Forest Loss A Record Breaking Crisis
May 26, 2025
