Millions Made From Exec Office365 Inboxes: FBI Investigation
Table of Contents
The Modus Operandi: How Hackers Target Executive Office365 Accounts
Cybercriminals employ sophisticated tactics to breach the seemingly impenetrable security of Office365 executive inboxes. These attacks are highly targeted and often exploit human error rather than solely relying on technical vulnerabilities. The goal is simple: access high-value accounts to execute financial fraud.
-
Spear Phishing: This is a common entry point. Hackers craft incredibly realistic emails mimicking legitimate communications from trusted sources, such as colleagues, clients, or even the CEO. These emails often contain malicious attachments or links leading to phishing websites designed to steal credentials. The personalization and urgency in these emails increase their success rate.
-
Credential Stuffing: Using lists of stolen usernames and passwords obtained from previous data breaches, hackers attempt to brute-force their way into executive accounts. This often involves automated tools that test combinations until a successful login is achieved.
-
Malware and Keyloggers: Malicious software, often delivered via phishing emails or infected websites, can record keystrokes, capture login credentials, and monitor online activity, providing hackers with a constant stream of sensitive information. Keyloggers can silently steal passwords and other sensitive data without the user's knowledge.
-
Exploiting Vulnerabilities: While less frequent due to Microsoft's ongoing security updates, hackers may exploit previously unknown software vulnerabilities (zero-day exploits) to gain unauthorized access.
The sophistication lies in the targeting. Executives are prime targets because their accounts often hold significant financial authority and access to sensitive corporate information. A successful breach involving an executive can result in substantial financial losses and reputational damage for the entire organization. News reports highlight numerous cases where executives have fallen victim to these highly targeted attacks, resulting in millions of dollars in losses.
The Scale of the Financial Losses: Millions Lost Through Office365 Executive Compromises
The FBI investigation underscores the staggering financial impact of compromised Office365 executive inboxes. Millions of dollars have been lost in the cases under investigation, a fraction of the billions lost globally to BEC scams annually. This isn't just about immediate monetary loss; it represents a significant blow to business stability and long-term success.
The types of financial crimes facilitated by these breaches include:
-
Wire Transfer Fraud: Hackers intercept or redirect wire transfer instructions, diverting funds to their own accounts.
-
Invoice Scams: They manipulate invoices, changing payment details to siphon money to fraudulent accounts.
-
Fake Payment Requests: Hackers impersonate vendors or suppliers, sending fraudulent payment requests to executives.
Beyond the immediate financial losses, businesses face:
-
Reputational damage: A data breach, especially one involving executive accounts, erodes trust with clients and investors.
-
Loss of investor confidence: Financial losses and reputational damage can severely impact a company's stock price and investment prospects.
-
Legal and regulatory costs: Businesses may face significant legal and regulatory fines for failing to adequately protect sensitive data.
The FBI's Response and Ongoing Investigation: Combating Office365 Executive Account Breaches
The FBI is actively investigating these BEC scams, collaborating with private sector companies to combat this growing threat. Their investigative strategies involve tracing the flow of funds, identifying the perpetrators, and working to recover stolen assets. They also provide crucial resources and guidance to victims.
The FBI’s Internet Crime Complaint Center (IC3) is a valuable resource for reporting cybercrimes, including BEC incidents. The IC3 offers assistance to victims and provides information on preventing future attacks. The FBI also actively shares best practices and security recommendations to help businesses protect themselves.
Preventing Future Attacks: Best Practices for Securing Office365 Executive Inboxes
The FBI, along with cybersecurity experts, strongly recommend the following preventative measures:
-
Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring multiple forms of authentication (e.g., password and a code from a mobile app) before granting access. This significantly reduces the risk of unauthorized access, even if credentials are compromised.
-
Regular Security Awareness Training: Educate employees about phishing techniques, social engineering tactics, and the importance of recognizing suspicious emails. Regular training keeps employees vigilant against evolving threats.
-
Strong Password Policies: Enforce strong password requirements, including length, complexity, and regular changes. Password managers can help employees create and manage complex, unique passwords for each account.
-
Advanced Threat Protection: Utilize Microsoft's advanced security features within Office365, such as anti-phishing filters, malware detection, and advanced threat analytics. These tools proactively identify and block malicious emails and attachments.
-
Regular Security Audits: Conduct routine security assessments to identify vulnerabilities and weaknesses in your Office365 environment. Regular audits help identify and address potential security gaps.
Conclusion: Protecting Your Business from Office365 Executive Inbox Attacks
The FBI investigation highlights the critical vulnerability of Office365 executive inboxes to sophisticated BEC attacks. The financial losses are substantial, and the consequences can be devastating for businesses. The good news is that proactive security measures can significantly mitigate this risk. By implementing multi-factor authentication, conducting regular security awareness training, enforcing strong password policies, utilizing advanced threat protection, and performing regular security audits, businesses can protect their valuable assets and avoid becoming victims of these costly attacks. Secure your Office365 executive inboxes today. Protect your business from BEC attacks. Learn more about protecting against Office365 breaches and take the necessary steps to secure your organization.

Featured Posts
-
 Jeanine Pirro A Closer Look At Her Legal Career And Public Profile
May 09, 2025
Jeanine Pirro A Closer Look At Her Legal Career And Public Profile
May 09, 2025 -
 Why Did Williams Let Colapinto Join Alpine Understanding The Driver Transfer
May 09, 2025
Why Did Williams Let Colapinto Join Alpine Understanding The Driver Transfer
May 09, 2025 -
 The Los Angeles Wildfires A Reflection Of Our Societal Obsession With Disaster Gambling
May 09, 2025
The Los Angeles Wildfires A Reflection Of Our Societal Obsession With Disaster Gambling
May 09, 2025 -
 Is Palantir Stock A Buy Before May 5th Analyst Predictions And Analysis
May 09, 2025
Is Palantir Stock A Buy Before May 5th Analyst Predictions And Analysis
May 09, 2025 -
 Sno Og Vanskelige Kjoreforhold I Sor Norge Vaer Forberedt
May 09, 2025
Sno Og Vanskelige Kjoreforhold I Sor Norge Vaer Forberedt
May 09, 2025
Latest Posts
-
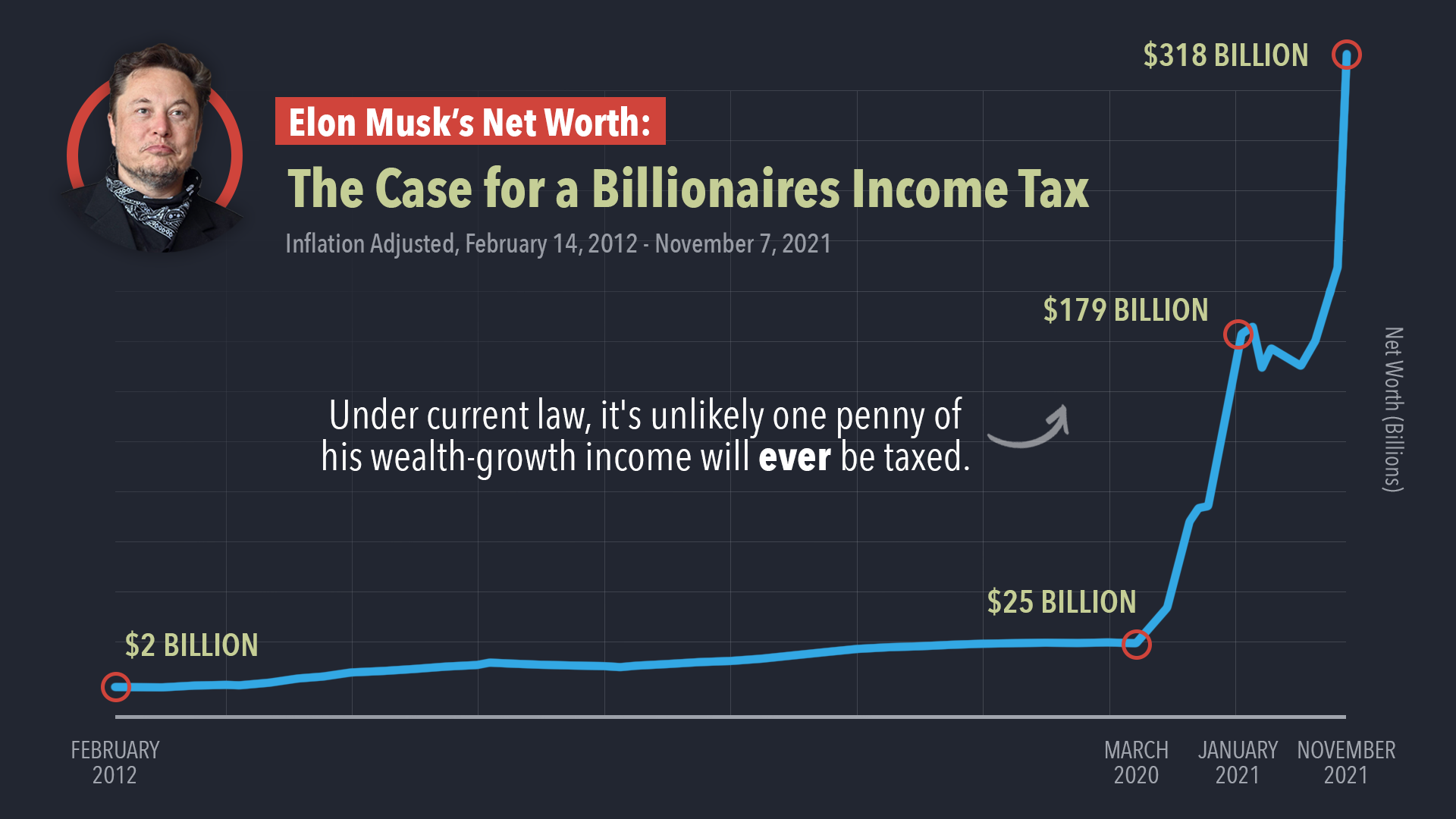 Examining The Relationship Between Us Economic Power And Elon Musks Wealth
May 10, 2025
Examining The Relationship Between Us Economic Power And Elon Musks Wealth
May 10, 2025 -
 Fluctuations In Elon Musks Net Worth Correlation With Us Economic Trends
May 10, 2025
Fluctuations In Elon Musks Net Worth Correlation With Us Economic Trends
May 10, 2025 -
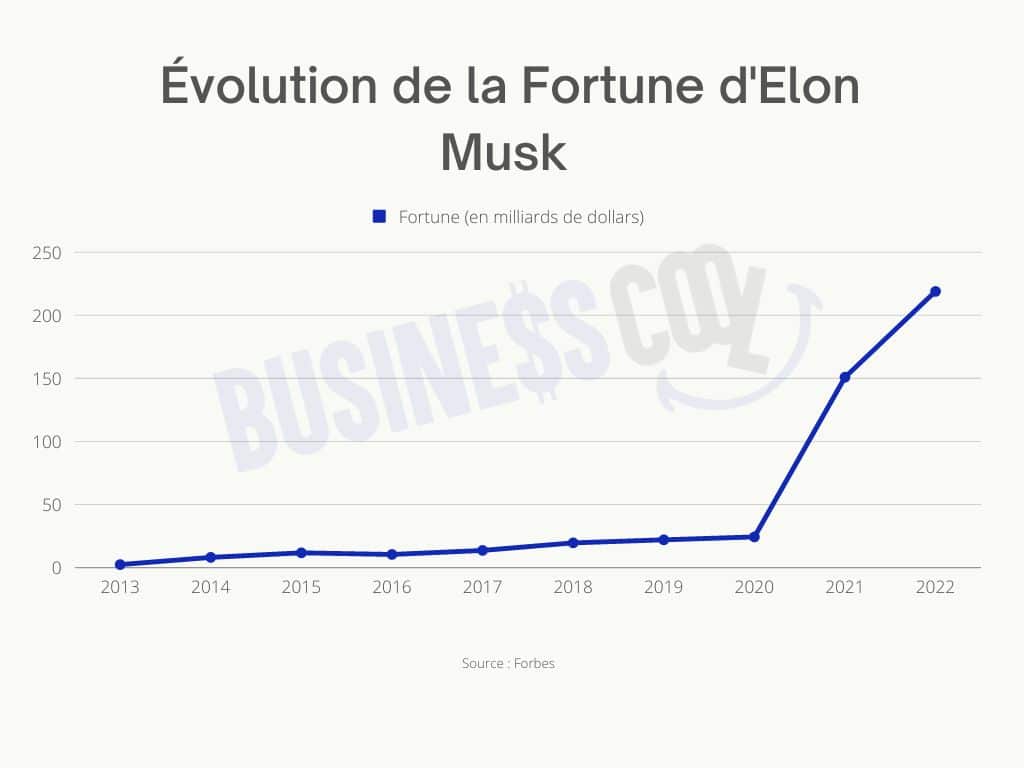 Teslas Success And Elon Musks Fortune An Examination Of Us Economic Factors
May 10, 2025
Teslas Success And Elon Musks Fortune An Examination Of Us Economic Factors
May 10, 2025 -
 Analyzing Elon Musks Net Worth The Role Of Us Economic Conditions
May 10, 2025
Analyzing Elon Musks Net Worth The Role Of Us Economic Conditions
May 10, 2025 -
 The Tesla Dogecoin Connection Analyzing The Recent Market Volatility
May 10, 2025
The Tesla Dogecoin Connection Analyzing The Recent Market Volatility
May 10, 2025
